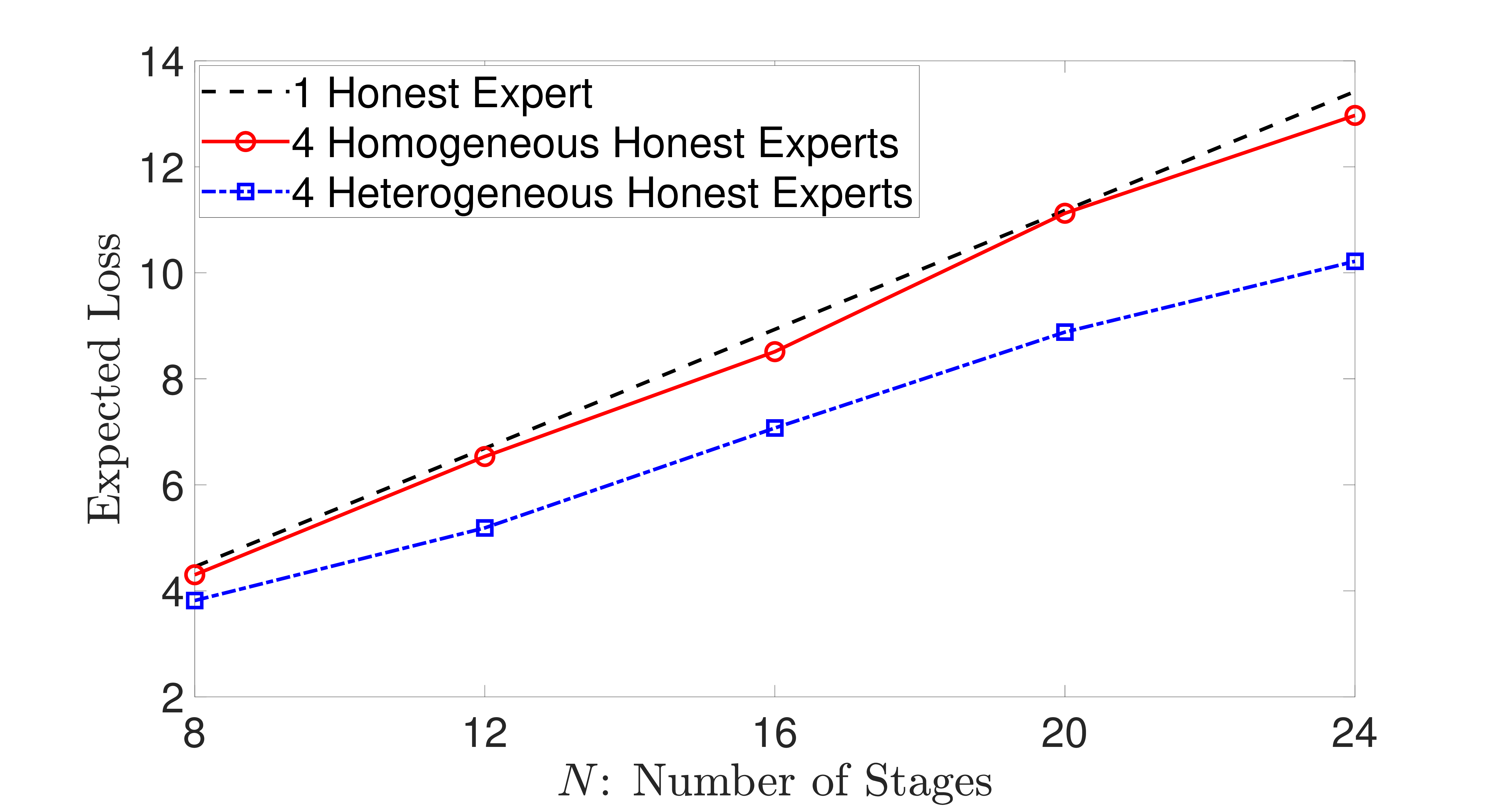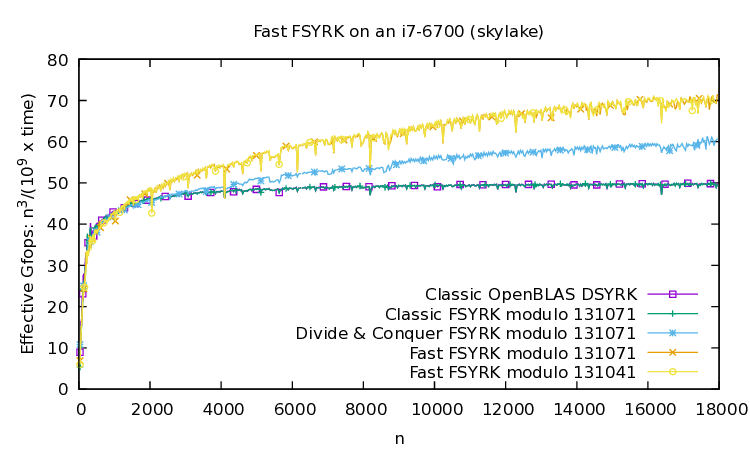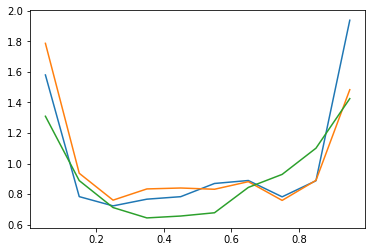
A simple microstructural explanation of the concavity of price impact
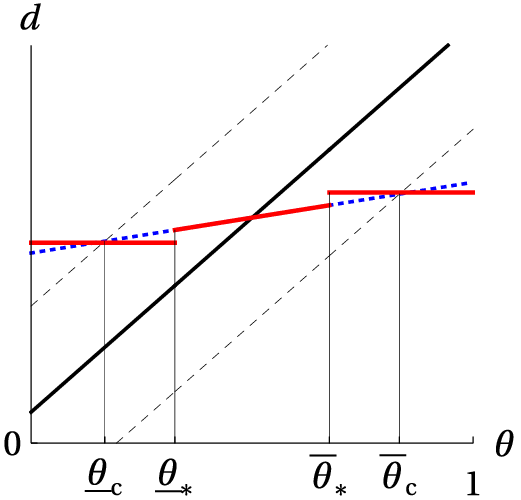
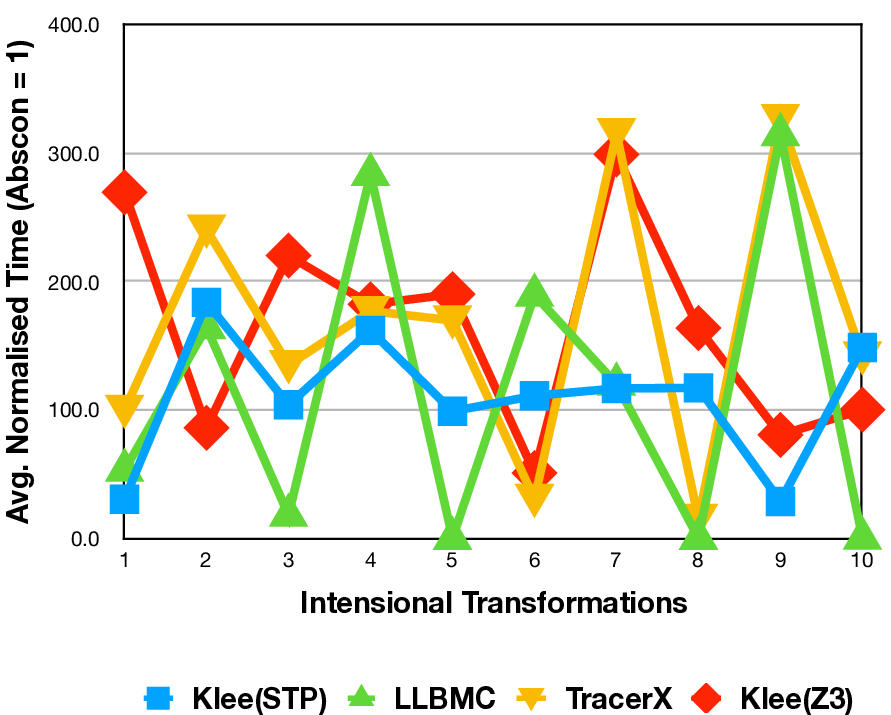
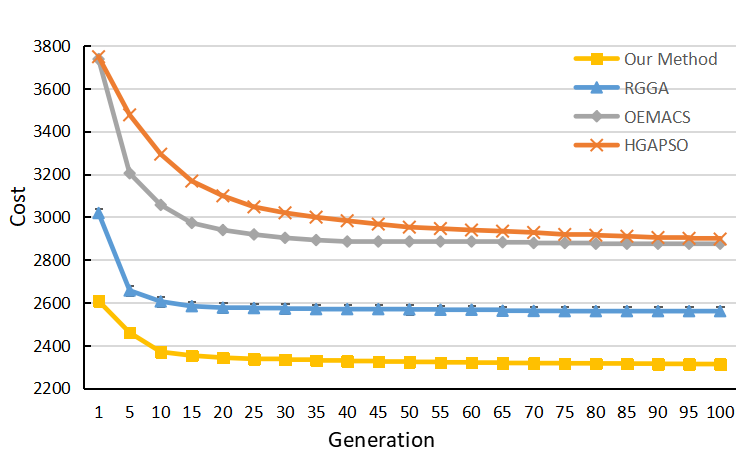
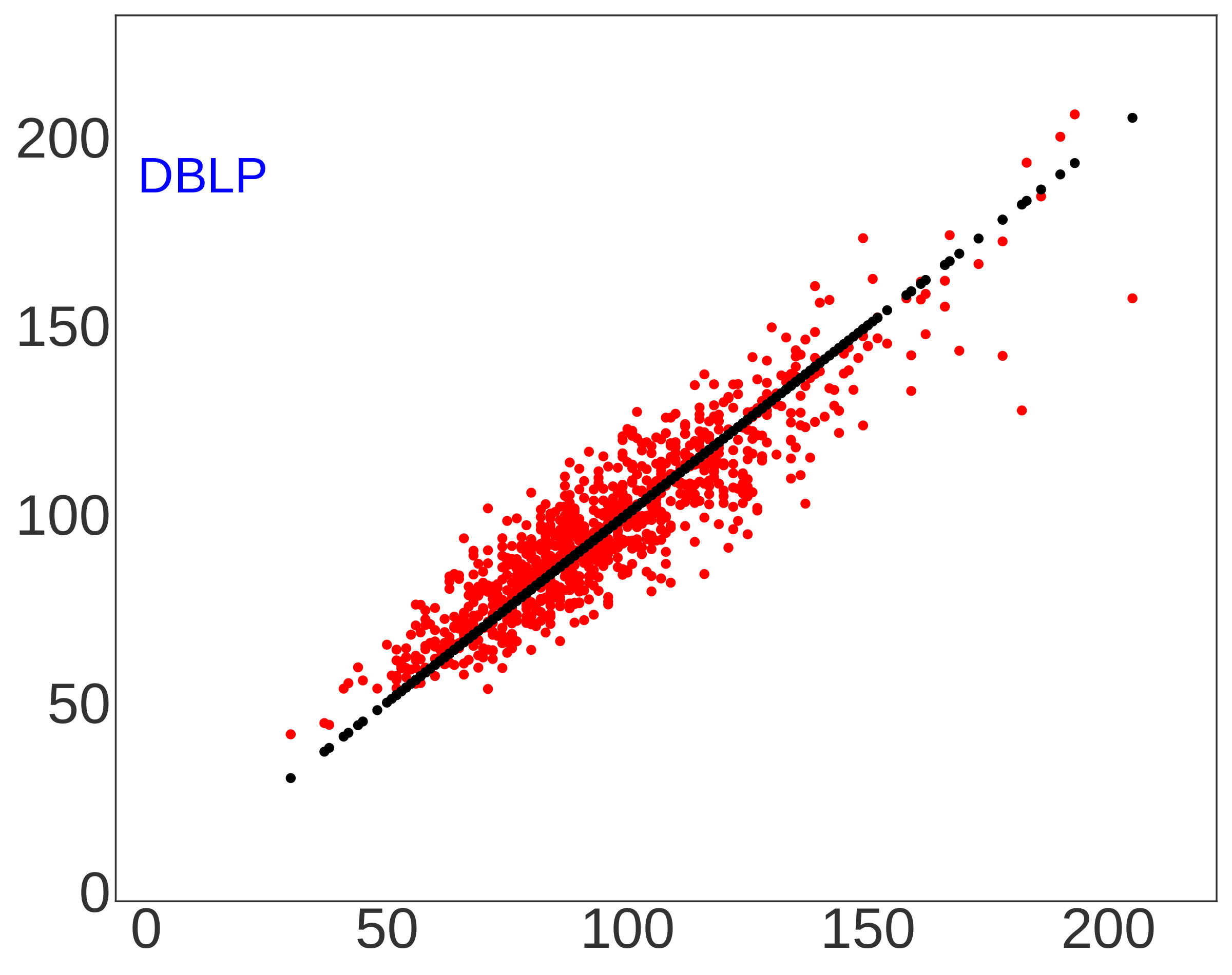
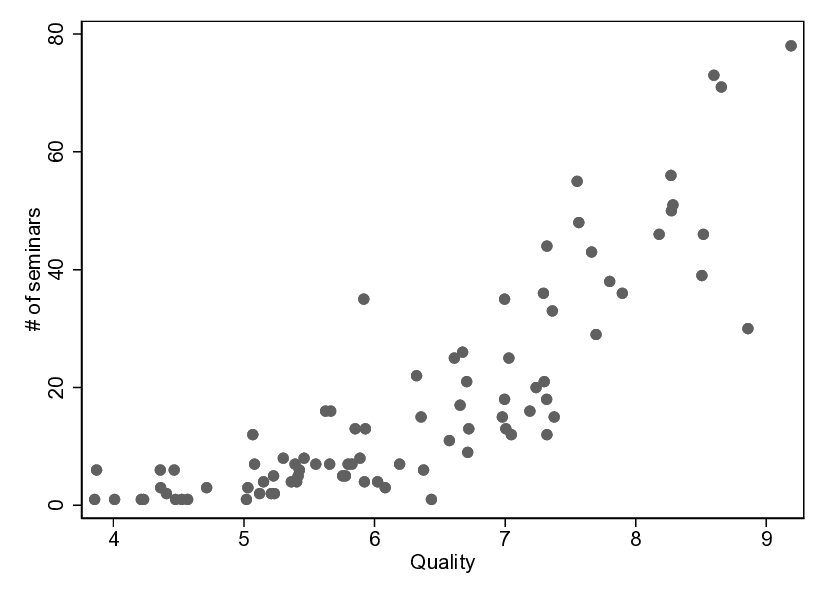
📝 Original Info Title: A simple microstructural explanation of the concavity of price impact ArXiv ID: 2001.01860 Date: 2020-12-15 Authors: Sergey Nadtochiy 📝 Abstract This article provides a simple explanation of the asymptotic concavity of the …