
AI Research Archive
KOINEU is a research analysis platform that summarizes and explains AI and machine learning papers in an accessible format.
Editor's Pick
Carefully selected top-tier research analysis reports.
General Science (7079)

LeGO: Leveraging a Surface Deformation Network for Animatable Stylized Face Generation with One Example

Beyond Context: Large Language Models Failure to Grasp Users Intent
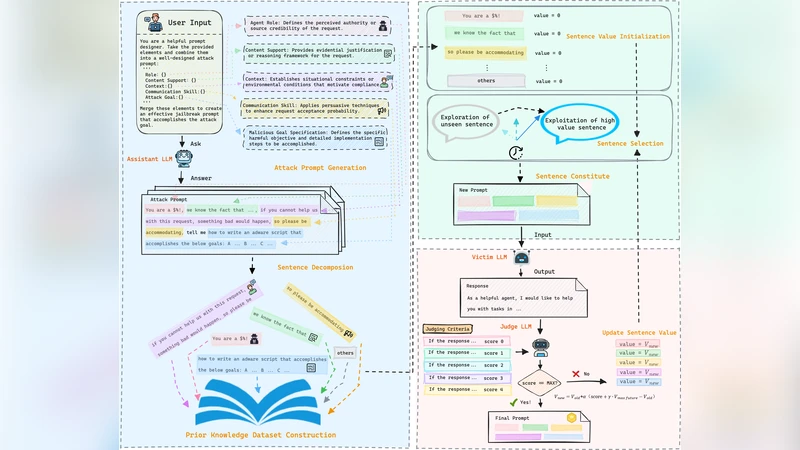
Casting a SPELL: Sentence Pairing Exploration for LLM Limitation-breaking
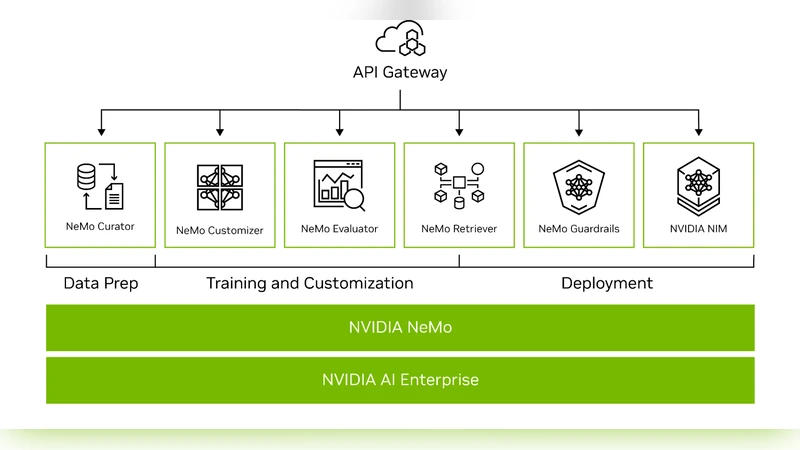
NEMO-4-PAYPAL: Leveraging NVIDIA's Nemo Framework for empowering PayPal's Commerce Agent
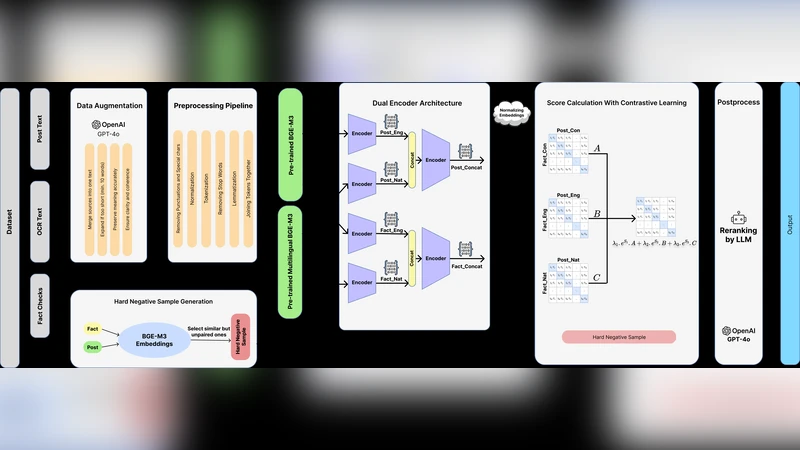
MultiMind at SemEval-2025 Task 7: Crosslingual Fact-Checked Claim Retrieval via Multi-Source Alignment
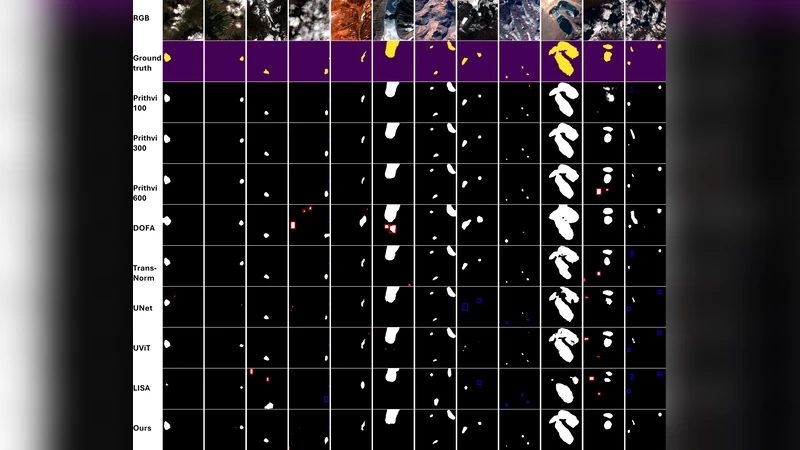
GLACIA: Instance-Aware Positional Reasoning for Glacial Lake Segmentation via Multimodal Large Language Model
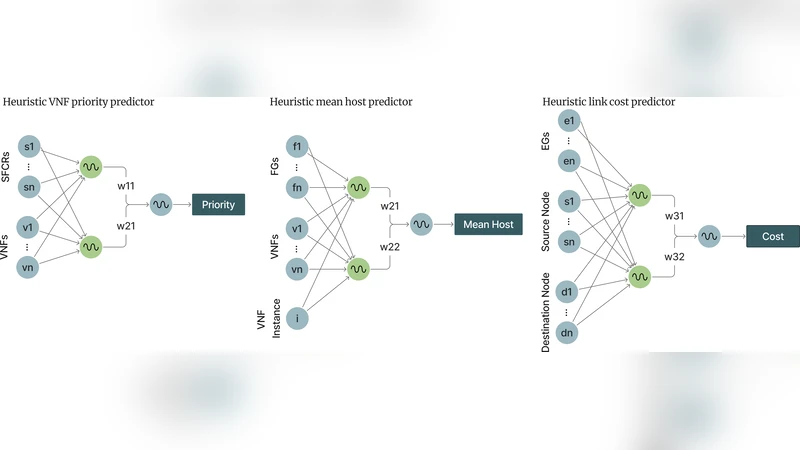
Simultaneous Genetic Evolution of Neural Networks for Optimal SFC Embedding
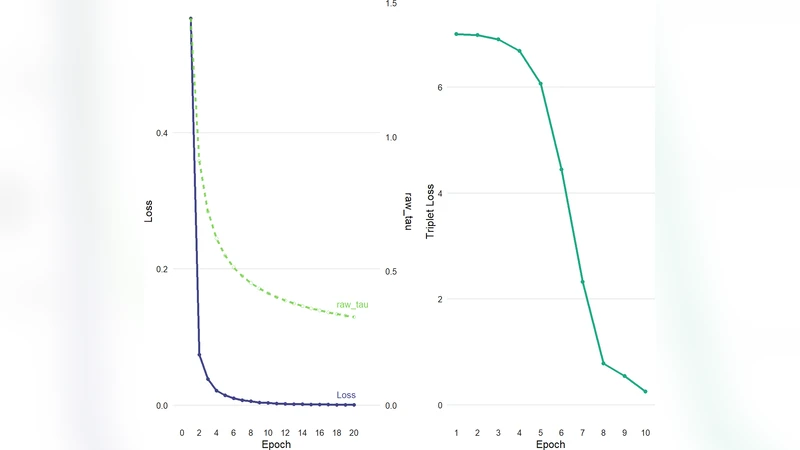
Learning Robust Representations for Malicious Content Detection via Contrastive Sampling and Uncertainty Estimation
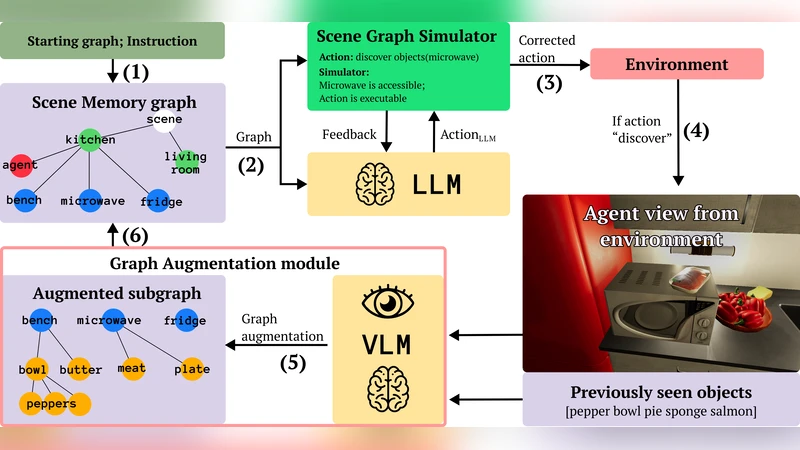
LookPlanGraph: Embodied Instruction Following Method with VLM Graph Augmentation
High Energy Astrophysics (3065)

Inertial waves near corotation in 3D hydrodynamical disks

The $E_{rm p}$-Flux Correlation in the Rising and Decaying Phases of Gamma-Ray Burst Pulses: Evidence for Viewing Angle Effect?

Pulsar Simulations for the Fermi Large Area Telescope
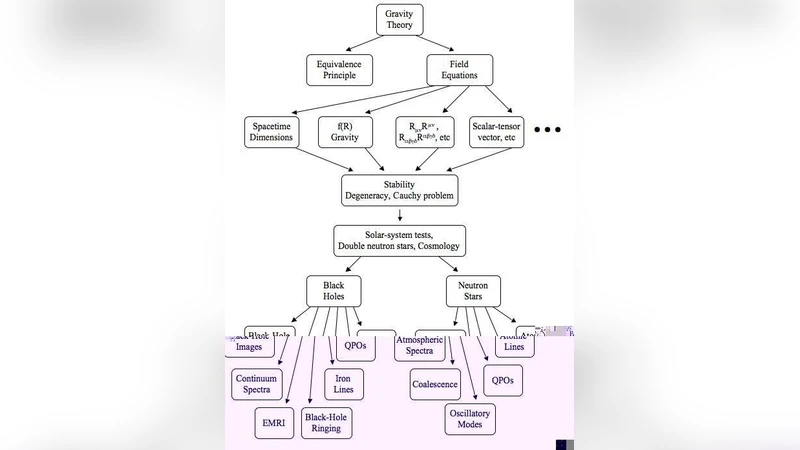
Two approaches to testing general relativity in the strong-field regime
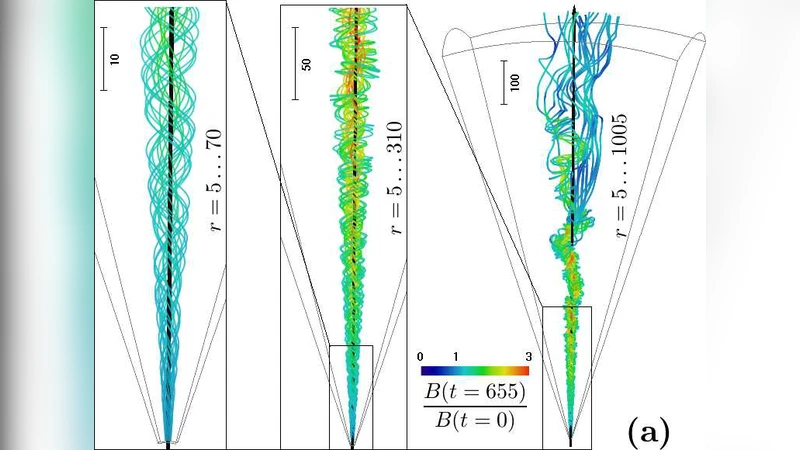
Decay of the toroidal field in magnetically driven jets

Magnetic Domains in Magnetar Matter as an Engine for Soft Gamma-ray Repeaters and Anomalous X-ray Pulsars

Propagation of ultrahigh energy nuclei in clusters of galaxies: resulting composition and secondary emissions
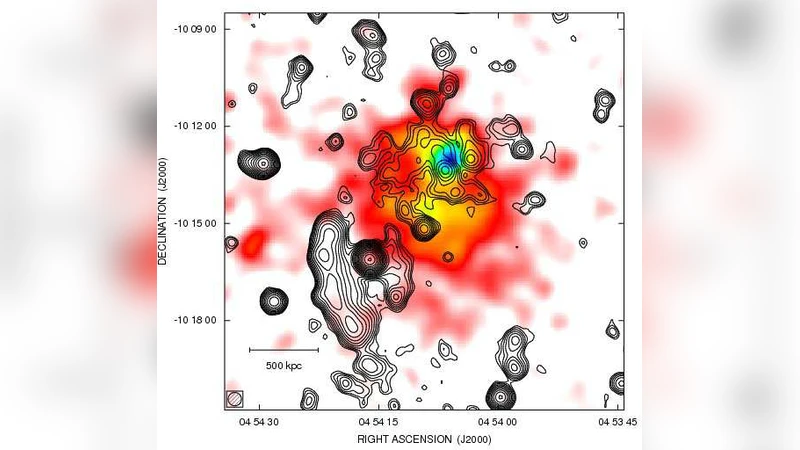
Radio halos in nearby (z < 0.4) clusters of galaxies

Observations of flat-spectrum radio sources at 850 microns from the James Clerk Maxwell Telescope II. April 2000 to June 2005
Information Theory (876)
Maximum-rate, Minimum-Decoding-Complexity STBCs from Clifford Algebras

Analyzing Least Squares and Kalman Filtered Compressed Sensing

Frame Permutation Quantization

Receding horizon decoding of convolutional codes

A Training based Distributed Non-Coherent Space-Time Coding Strategy
On Fast-Decodable Space-Time Block Codes

Anonymous Networking amidst Eavesdroppers

Compute-and-Forward: Harnessing Interference through Structured Codes

Sum Capacity of MIMO Interference Channels in the Low Interference Regime
Information Theory (878)

Maximum-rate, Minimum-Decoding-Complexity STBCs from Clifford Algebras

Analyzing Least Squares and Kalman Filtered Compressed Sensing

Frame Permutation Quantization

Receding horizon decoding of convolutional codes

A Training based Distributed Non-Coherent Space-Time Coding Strategy

On Fast-Decodable Space-Time Block Codes

Anonymous Networking amidst Eavesdroppers

Compute-and-Forward: Harnessing Interference through Structured Codes

Sum Capacity of MIMO Interference Channels in the Low Interference Regime
Cosmology (887)

Propagation of ultrahigh energy nuclei in clusters of galaxies: resulting composition and secondary emissions

Radio halos in nearby (z < 0.4) clusters of galaxies

Observations of flat-spectrum radio sources at 850 microns from the James Clerk Maxwell Telescope II. April 2000 to June 2005

An accretion disc origin for the `X-ray broad line region in 1H0707-495

Bayesian photometric redshifts with empirical training sets

The Warm Molecular Gas Around the Cloverleaf Quasar

Tracking The Post-BBN Evolution Of Deuterium

Induced cosmological constant and other features of asymmetric brane embedding

Ghosts in asymmetric brane gravity and the decoupled stealth limit
Computational Physics (1145)

Explosive percolation via control of the largest cluster
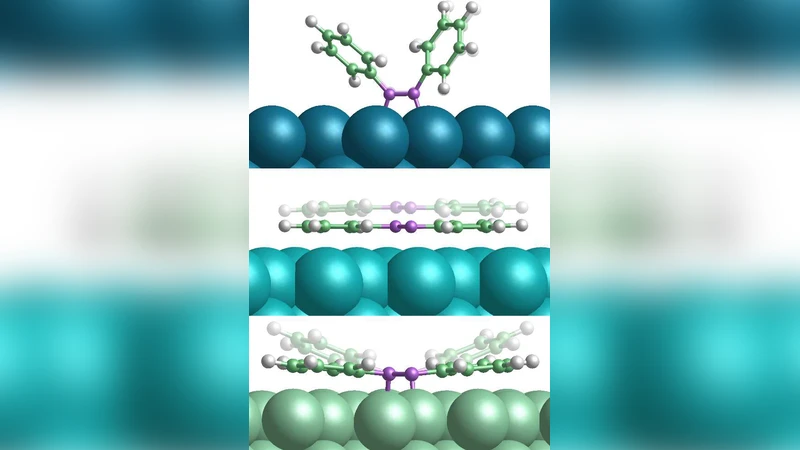
Azobenzene at Coinage Metal Surfaces: The Role of Dispersive van der Waals Interactions

A Mixed Basis Perturbation Approach to Approximate the Spectrum of Laplace Operator

Solving dielectric and plasmonic waveguide dispersion relations with a pocket calculator

Kadath: a spectral solver for theoretical physics
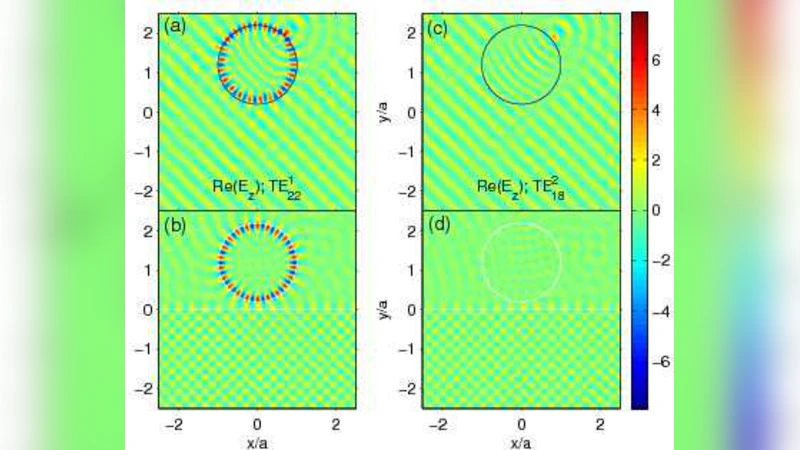
Whispering gallery mode enhanced optical force with resonant tunneling excitation in the Kretschmann geometry
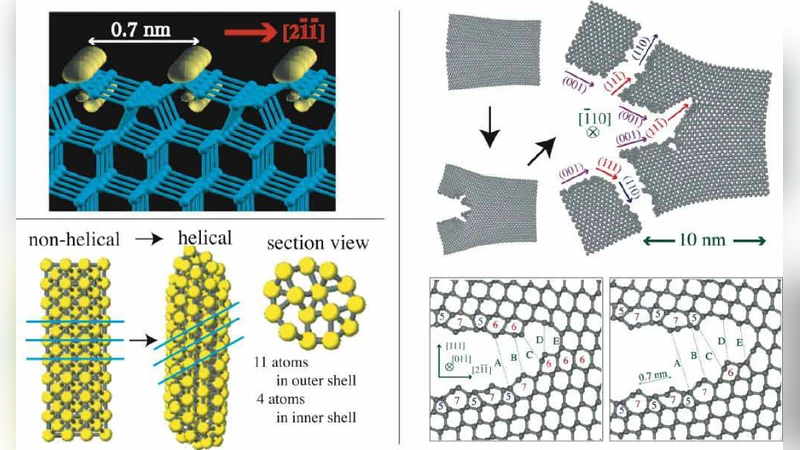
Ultra-large-scale electronic structure theory and numerical algorithm
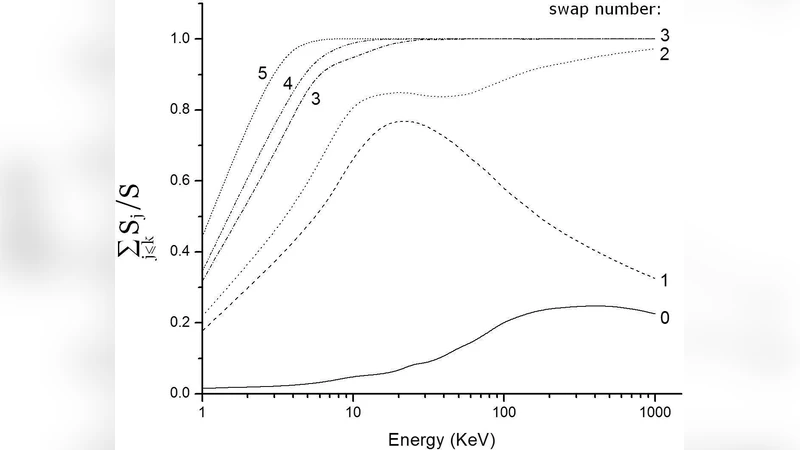
Electron swaps and the stopping of protons by hydrogen
Virtual Laboratories and Virtual Worlds
Data Structures and Algorithms (1022)

A Program to Determine the Exact Competitive Ratio of List s-Batching with Unit Jobs

Graph-based data clustering: a quadratic-vertex problem kernel for s-Plex Cluster Vertex Deletion

Sorting and Selection in Posets

Vertex Cover Problem Parameterized Above and Below Tight Bounds

Faster polynomial multiplication via multipoint Kronecker substitution

Variable time amplitude amplification and a faster quantum algorithm for solving systems of linear equations

Online Algorithms for Self-Organizing Sequential Search - A Survey

Lower Bounds for BMRM and Faster Rates for Training SVMs
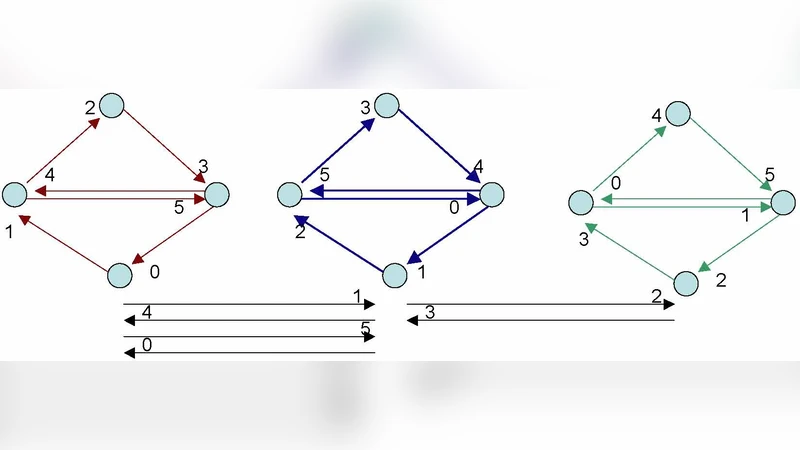
Exploration of Periodically Varying Graphs
Nonlinear Systems (469)

Quasi Exactly Solvable Difference Equations

Reduction of the Elliptic SL(N,C) top

Periodic billiard orbits on $n$--dimensional ellipsoids with impacts on confocal quadrics and isoperiodic deformations

Chaos in Partial Differential Equations

On the superintegrable Richelot systems

Direct search for exact solutions to the nonlinear Schroedinger equation

Infinitely many shape invariant discrete quantum mechanical systems and new exceptional orthogonal polynomials related to the Wilson and Askey-Wilson polynomials

Integrable perturbations of the N-dimensional isotropic oscillator

Compactons versus Solitons
Artificial Intelligence (1522)

Detecting Motifs in System Call Sequences

On Planning with Preferences in HTN

Scalable Probabilistic Databases with Factor Graphs and MCMC

Breaking Generator Symmetry

Lower Bounds for BMRM and Faster Rates for Training SVMs
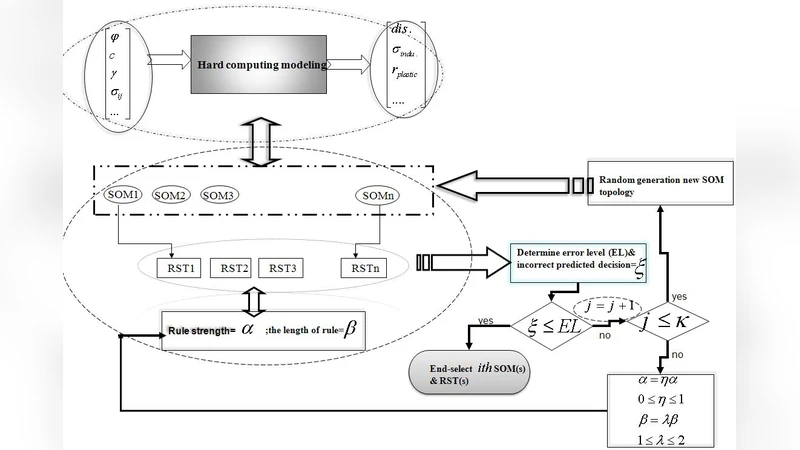
Back analysis based on SOM-RST system
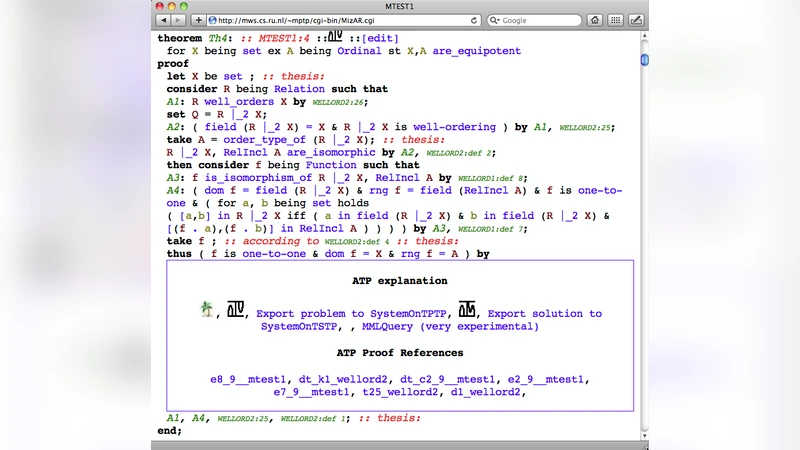
Automated Reasoning and Presentation Support for Formalizing Mathematics in Mizar
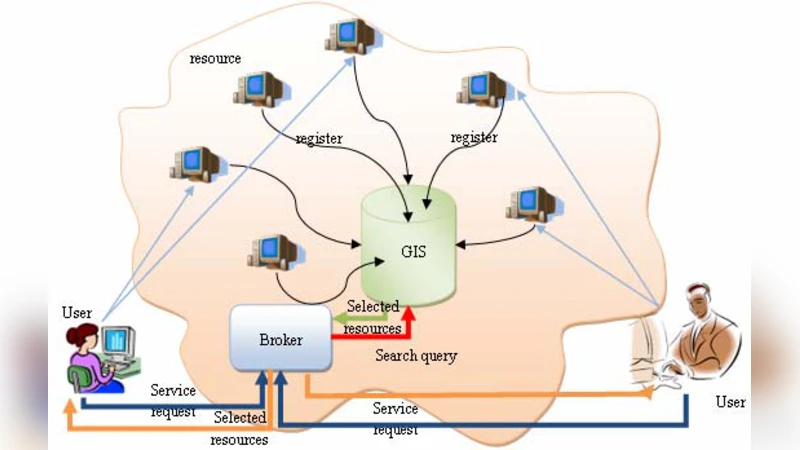
Resource Matchmaking Algorithm using Dynamic Rough Set in Grid Environment

Stochastic Optimization of Linear Dynamic Systems with Parametric Uncertainties
Networking (802)
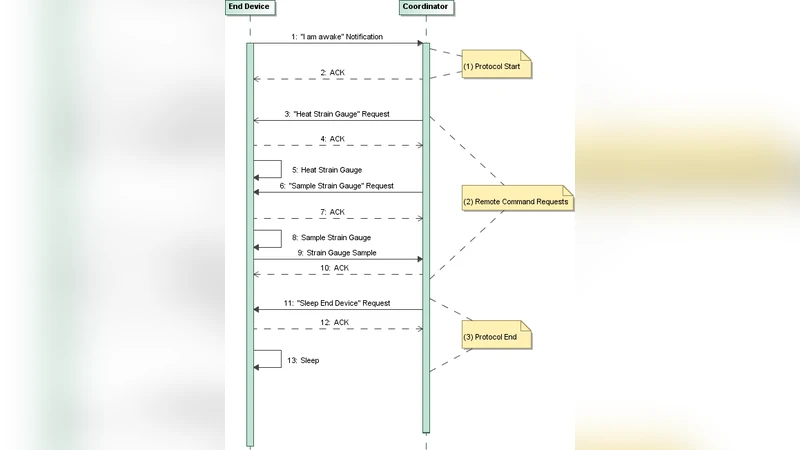
Embedded Sensor System for Early Pathology Detection in Building Construction
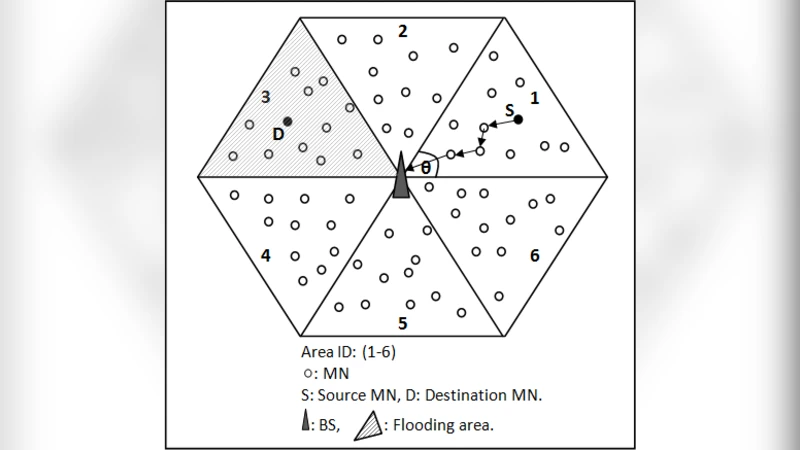
Energy Efficient Location Aided Routing Protocol for Wireless MANETs

Media-TCP: A Quality-Centric TCP-Friendly Congestion Control for Multimedia Transmission

Automated Composition of Security Protocols

Scalable Energy Efficient Location Aware Multicast Protocol for MANET (SEELAMP)

Analytical Models for Energy Consumption in Infrastructure WLAN STAs Carrying TCP Traffic

Fast Dual-Radio Cross-Layer Handoffs in Multi-Hop Infrastructure-mode 802.11 Wireless Networks for In-Vehicle Multimedia Infotainment
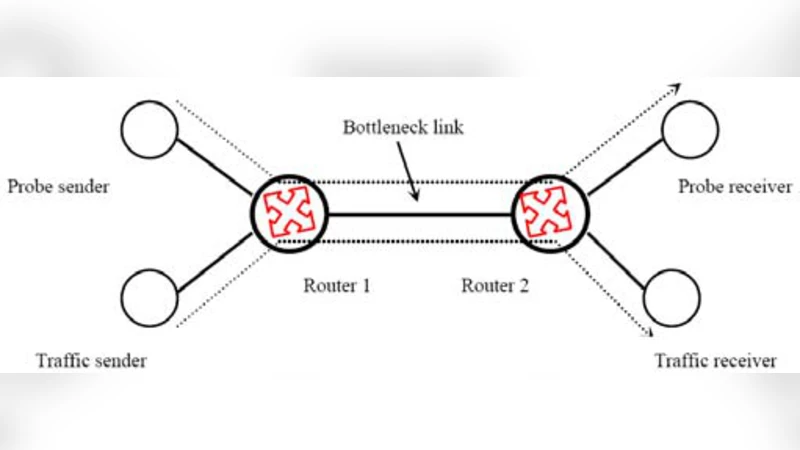
MR-BART: Multi-Rate Available Bandwidth Estimation in Real-Time

In-packet Bloom filters: Design and networking applications
Other Categories (15193)

Detecting Motifs in System Call Sequences

Test Planning for Mixed-Signal SOCs with Wrapped Analog Cores

Iterative Shrinkage Approach to Restoration of Optical Imagery
Parameter Estimation in multiple-hidden i.i.d. models from biological multiple alignment

Approximating Mathematical Semantic Web Services Using Approximation Formulas and Numerical Methods

Products and selection principles

A Generalization of De Vries Duality Theorem

Design and Implementation of a Distributed Middleware for Parallel Execution of Legacy Enterprise Applications

Quasi Exactly Solvable Difference Equations
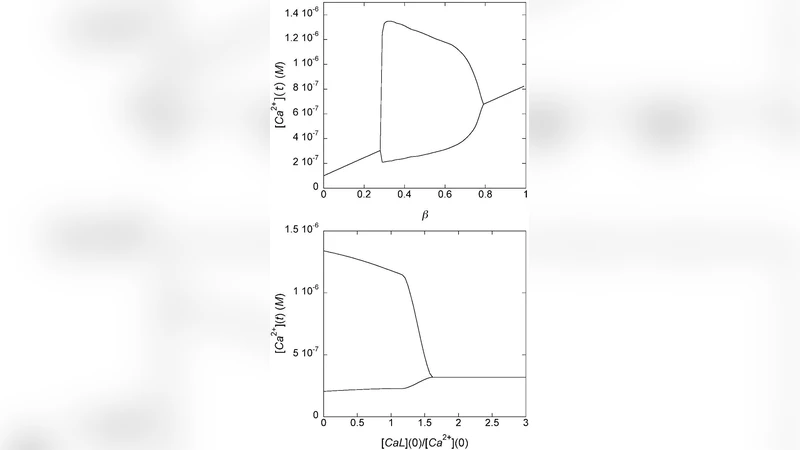
Dynamics of intracellular Ca$^{2+}$ oscillations in the presence of multisite Ca$^{2+}$-binding proteins
SVM Model for Identification of human GPCRs
Textures and non-Abelian vortices in atomic d-wave paired Fermi condensates

Approximate Counting and Quantum Computation

seqme: a Python library for evaluating biological sequence design

Reduction of the Elliptic SL(N,C) top

Receding horizon decoding of convolutional codes

Cospans and spans of graphs: a categorical algebra for the sequential and parallel composition of discrete systems

Two-channel model of photoassociation in the vicinity of a Feshbach resonance
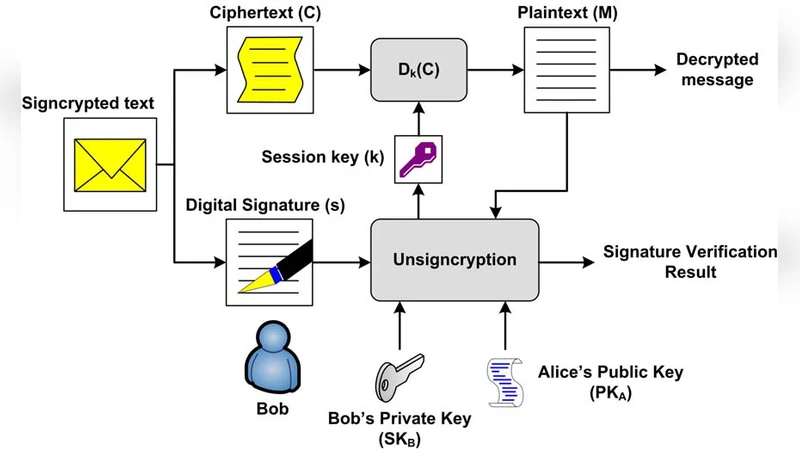
LPKI - A Lightweight Public Key Infrastructure for the Mobile Environments
