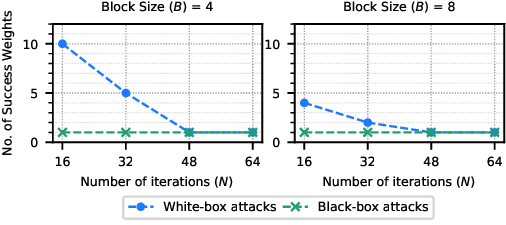
Edge AI inference is becoming prevalent thanks to the emergence of small yet high-performance microprocessors. This shift from cloud to edge processing brings several benefits in terms of energy savings, improved latency, and increased privacy. On the downside, bringing computation to the edge makes them more vulnerable to physical side-channel attacks (SCA), which aim to extract the confidentiality of neural network models, e.g., architecture and weight. To address this growing threat, we propose PermuteV, a performant side-channel resistant RISC-V core designed to secure neural network inference. PermuteV employs a hardware-accelerated defense mechanism that randomly permutes the execution order of loop iterations, thereby obfuscating the electromagnetic (EM) signature associated with sensitive operations. We implement PermuteV on FPGA and perform evaluations in terms of side-channel security, hardware area, and runtime overhead. The experimental results demonstrate that PermuteV can effectively defend against EM SCA with minimal area and runtime overhead.
Edge devices like smart home and IoT systems have become much more powerful recently, allowing them to perform complex tasks like neural network inference locally. This shift from cloud-based processing to edge computing offers numerous benefits, including reduced latency, lower power consumption, and enhanced user privacy. However, performing computation directly on these devices makes them more susceptible to sidechannel attacks (SCAs), which could allow attackers to steal the intellectual property stored on the devices, such as the weight and architecture of the neural network model.
Side-channel attacks exploit the physical characteristics of hardware devices such as power consumption and electromagnetic emanations, to extract sensitive information. Since the pioneering work of Kocher et al. [1], SCAs have been extensively studied, initially focusing on cryptographic algorithm implementations [2]- [4]. Recently, researchers have demonstrated the feasibility of applying SCAs to neural networks, extracting model architectures and weights through side-channel analysis [5]- [7].
Exposure of neural network (NN) models to SCAs poses significant risks. High-performance NN models, developed through extensive training and substantial resource investment, represent valuable intellectual property of the vendor. More importantly, the model’s internal architecture and parameters, if leaked, can aid attackers in performing adversarial attacks [8] or inferring sensitive training data [9]. Therefore, protecting these models from reverse engineering is a vital task.
Several defense mechanisms targeting NN hardware accelerators have been proposed based on shuffling and masking techniques [10]- [13]. While these methods achieve low runtime overhead, they often introduce substantial area overhead (up to 5.9x) and are not applicable to software-based NN implementation running on general-purpose microprocessors which are common way to deploy NN on edge devices [14]- [16]. Conversely, microarchitecture-level protections for microprocessors such as [17], [18] are only designed for and evaluated on cryptographic encryption workload. The only existing protection targeting NN workload on microprocessors is [7]. While effective on NN workloads and requiring no software modification, it incur significant runtime overhead (13.7% to 41.8%). This overhead hinders their adoption in resourceconstrained edge devices with strict latency requirements. Therefore, there is a clear need for effective countermeasures that can safeguard NN models on edge devices powered by general-purpose microprocessors with minimal overhead.
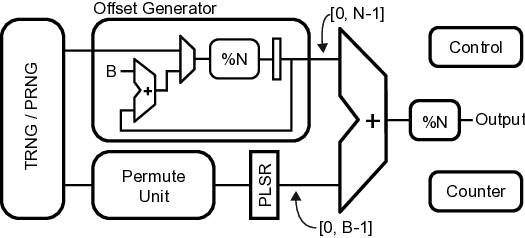
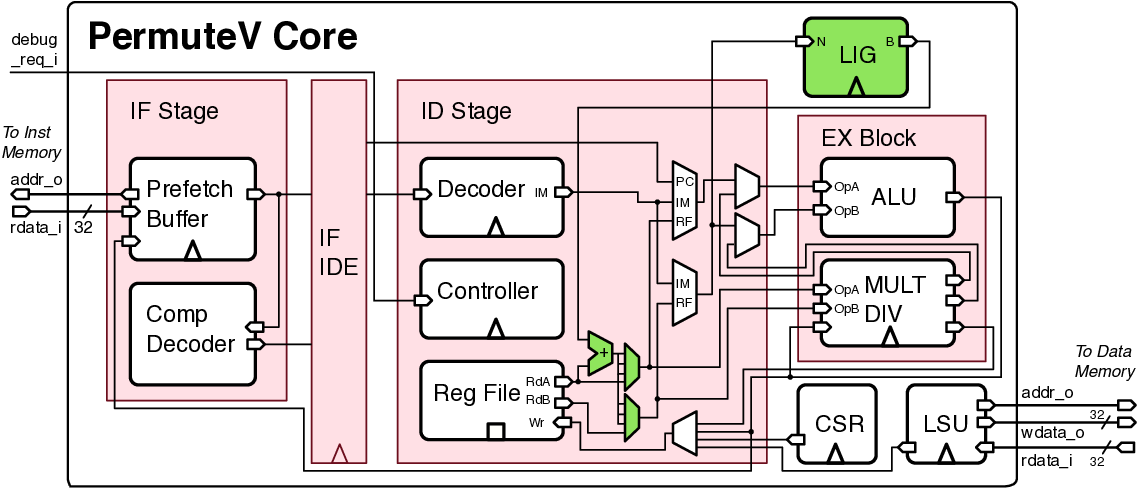
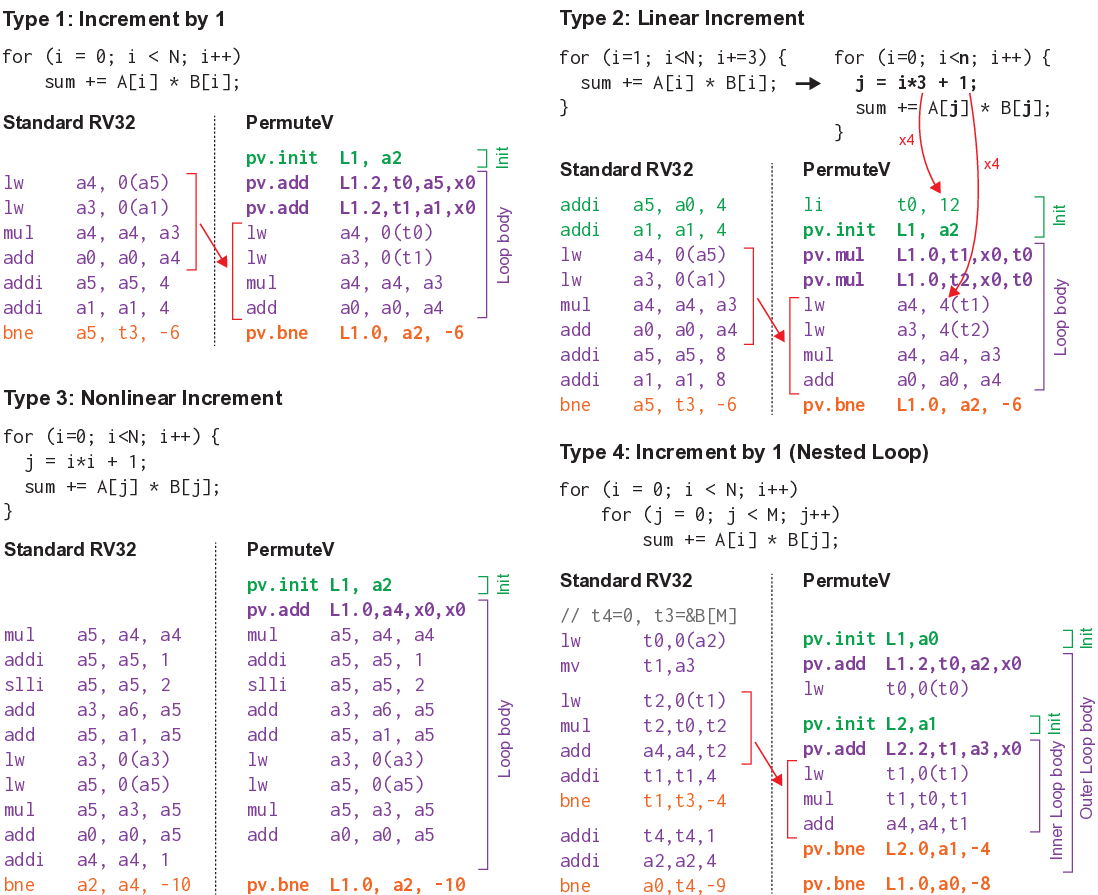
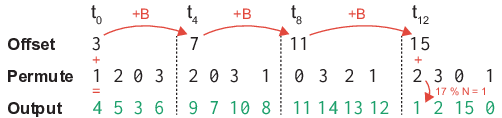
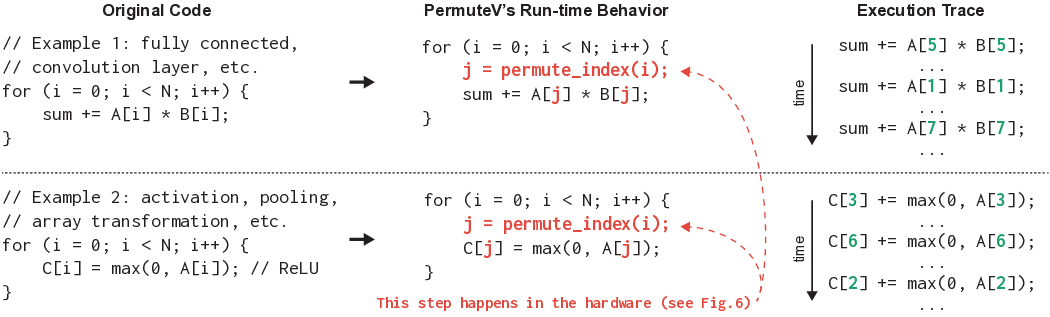
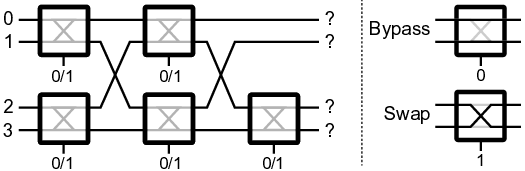
To address this pressing concern, this paper introduces PermuteV, a side-channel resistant RISC-V core design to secure neural network inference on edge devices against physical SCAs. We developed PermuteV on an open-source Ibex RISC-V core [19] to facilitate its adoption in real-world system on a chip (SoC) design. PermuteV incorporates a Loop Index Generator (LIG) module and custom instruction set architecture (ISA) extensions to permute the execution order of loop iterations with negligible performance overhead. To facilitate software development, we extended the LLVM compiler framework [20] to automatically generate code utilizing these custom ISA extensions. Our evaluation demonstrates that PermuteV’s permutation strategy effectively obfuscates electromagnetic emanations associated with sensitive computations, significantly hindering attackers’ ability to extract valuable information.
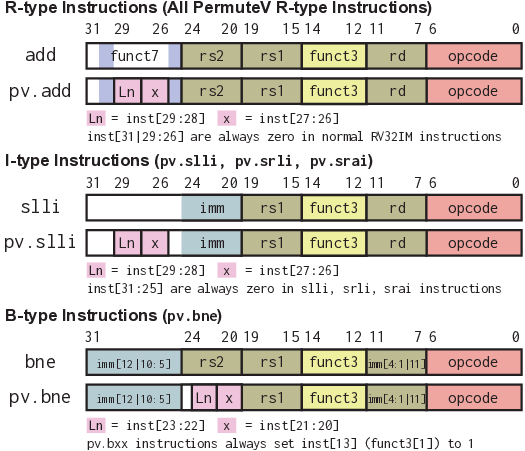
We make the following contributions in this work. 1) We present PermuteV, the first microarchitecture and software co-designed solution for secure neural network inference on general-purpose microprocessors. PermuteV integrates a Loop Index Generator (LIG) module to permute the loop iteration order, thwarting EM SCAs with negligible runtime overhead without requiring code modifications. 2) We propose RISC-V ISA extensions to leverage the LIG module. PermuteV custom instructions implicitly add the permuted loop iteration index to the source register value, enabling efficient hardware implementation and allowing the compiler to generate permuted loop code using the same number of instructions as in a sequential loop. 3) We implement PermuteV on an FPGA and evaluate its side-channel security and performance on a multiplyaccumulate (MAC) operation, which is the building block of the NN inference operation. PermuteV is fully compatible interface-wise with the popular open-source Ibex core [19], enabling its real-world use as a drop-in replacement core in many existing SoC design projects like PULP [21] and OpenTitan [22].
Side-channel attacks (SCAs) represent a significant threat to the security of various systems, including but not limited to cryptosystems. Unlike traditional attacks that exploit software vulnerabilities, SCAs target the physical characteristics of devices such as power consumption [1], electromagnetic (EM) emanations
This content is AI-processed based on open access ArXiv data.