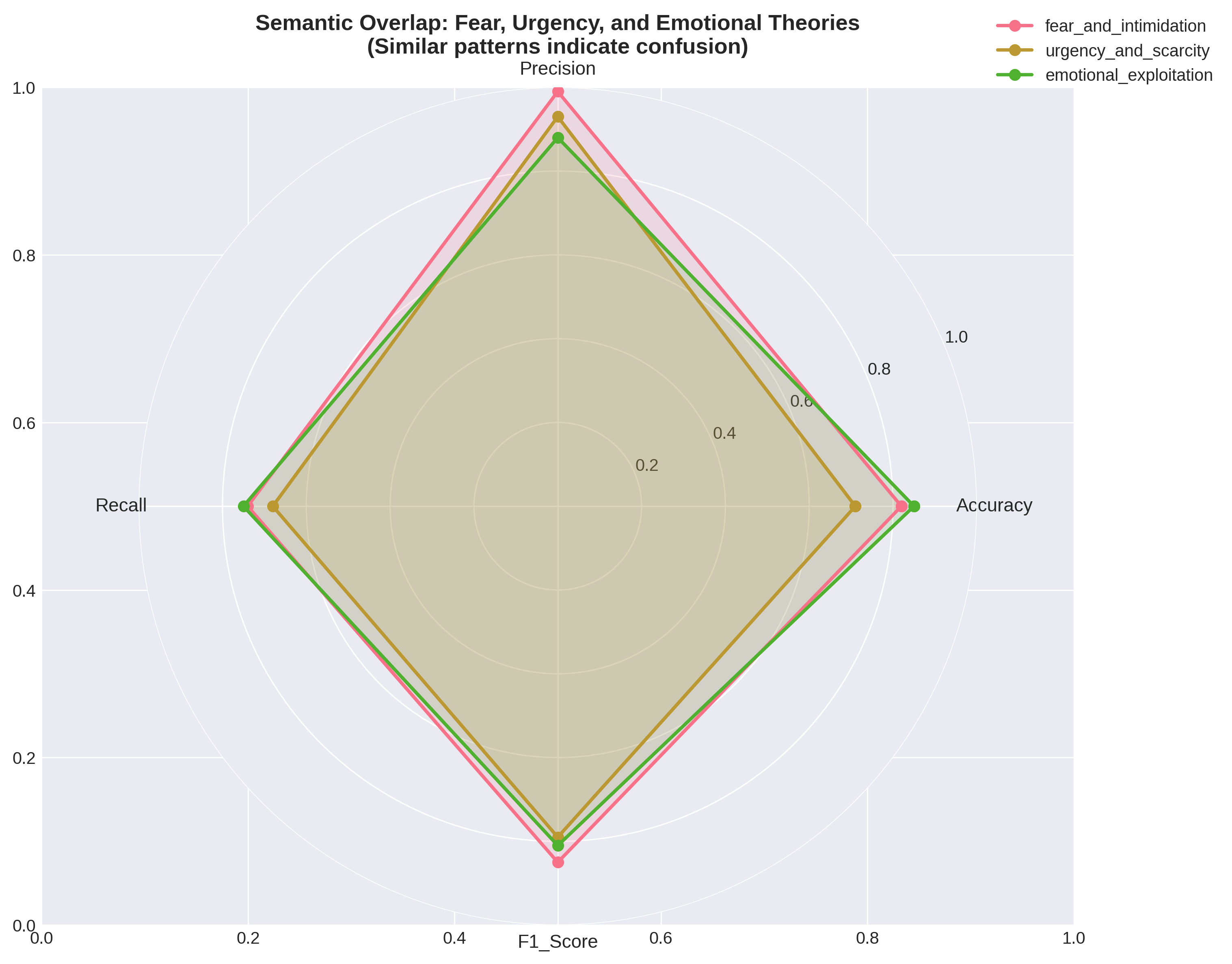
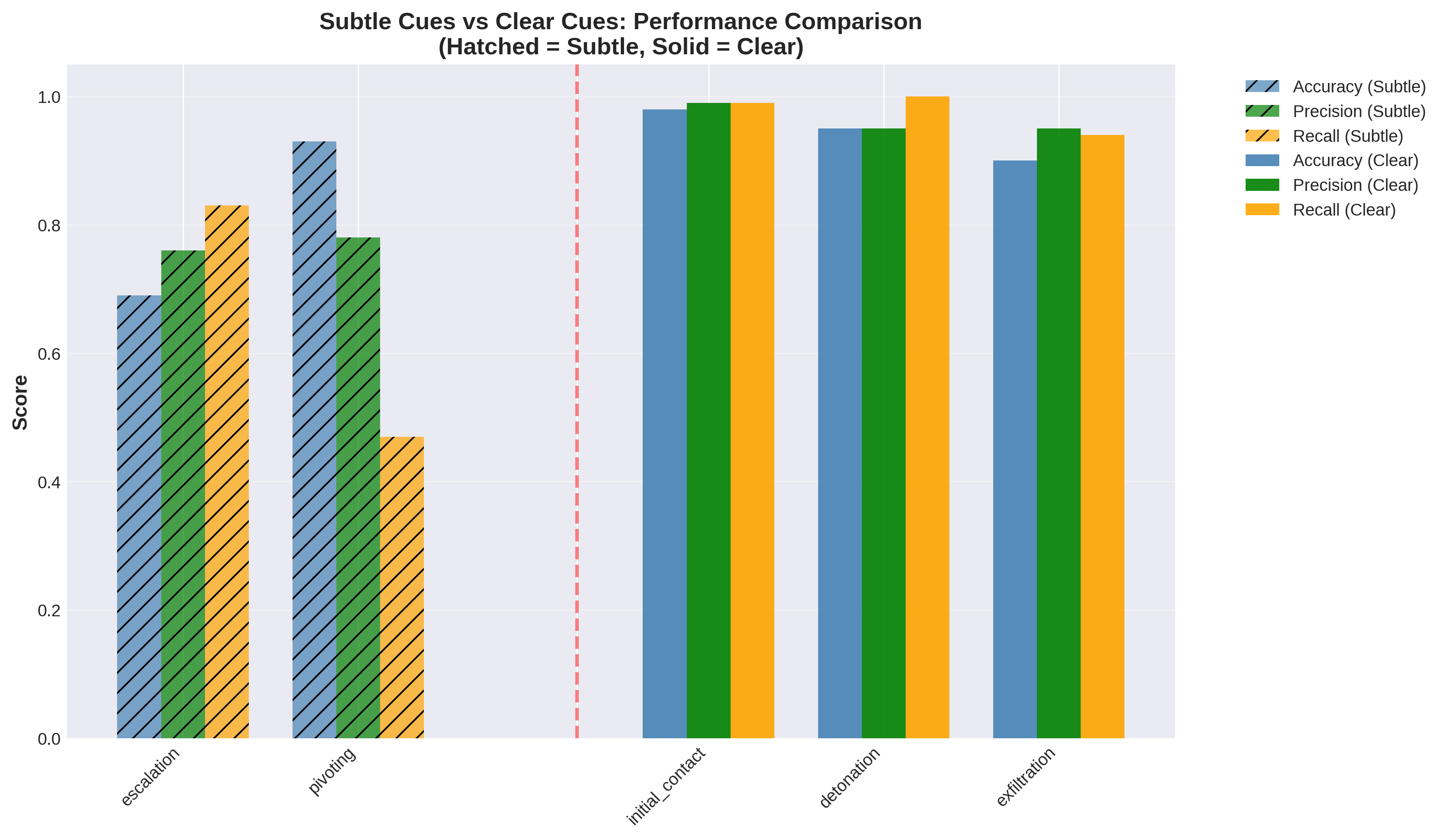
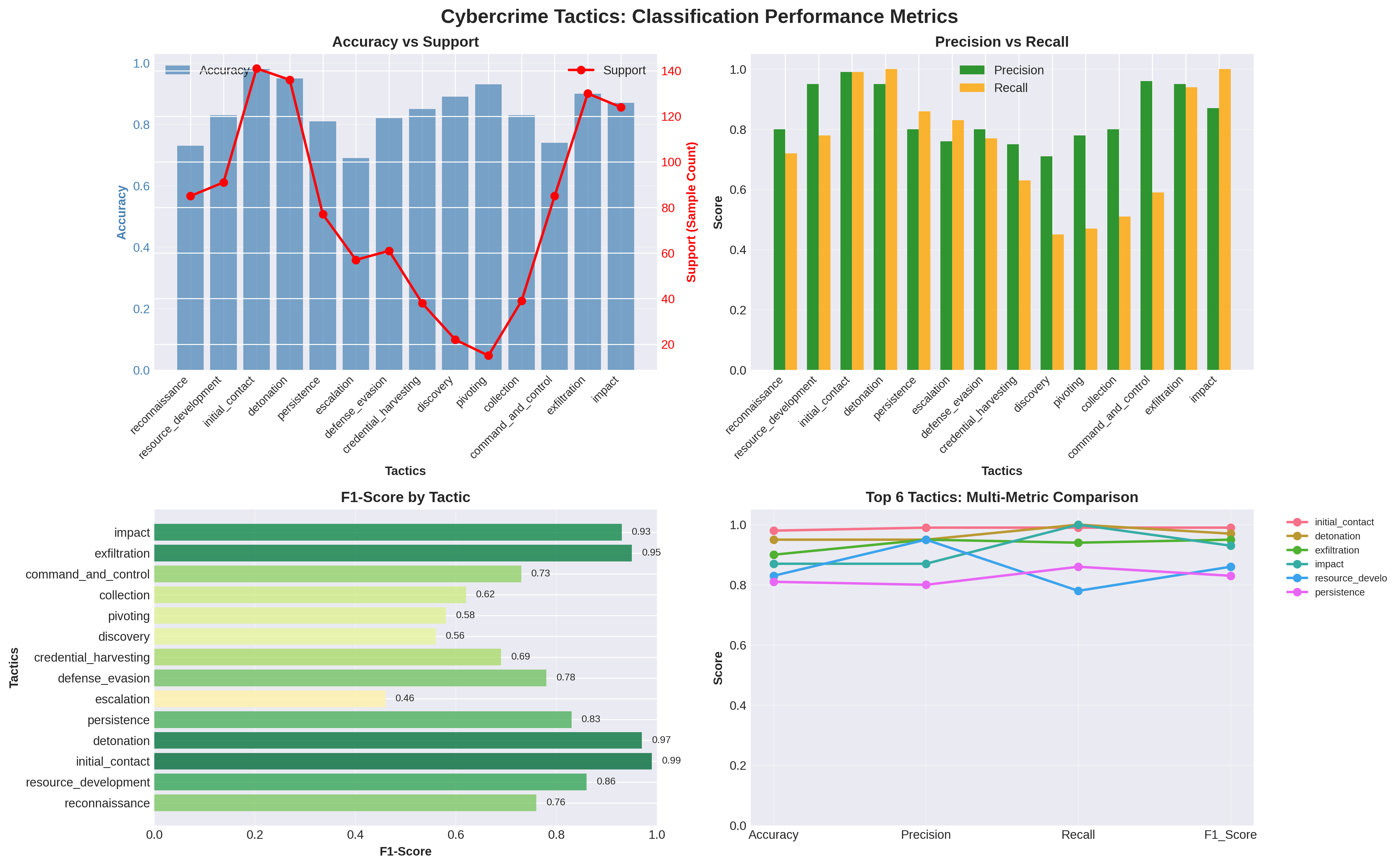
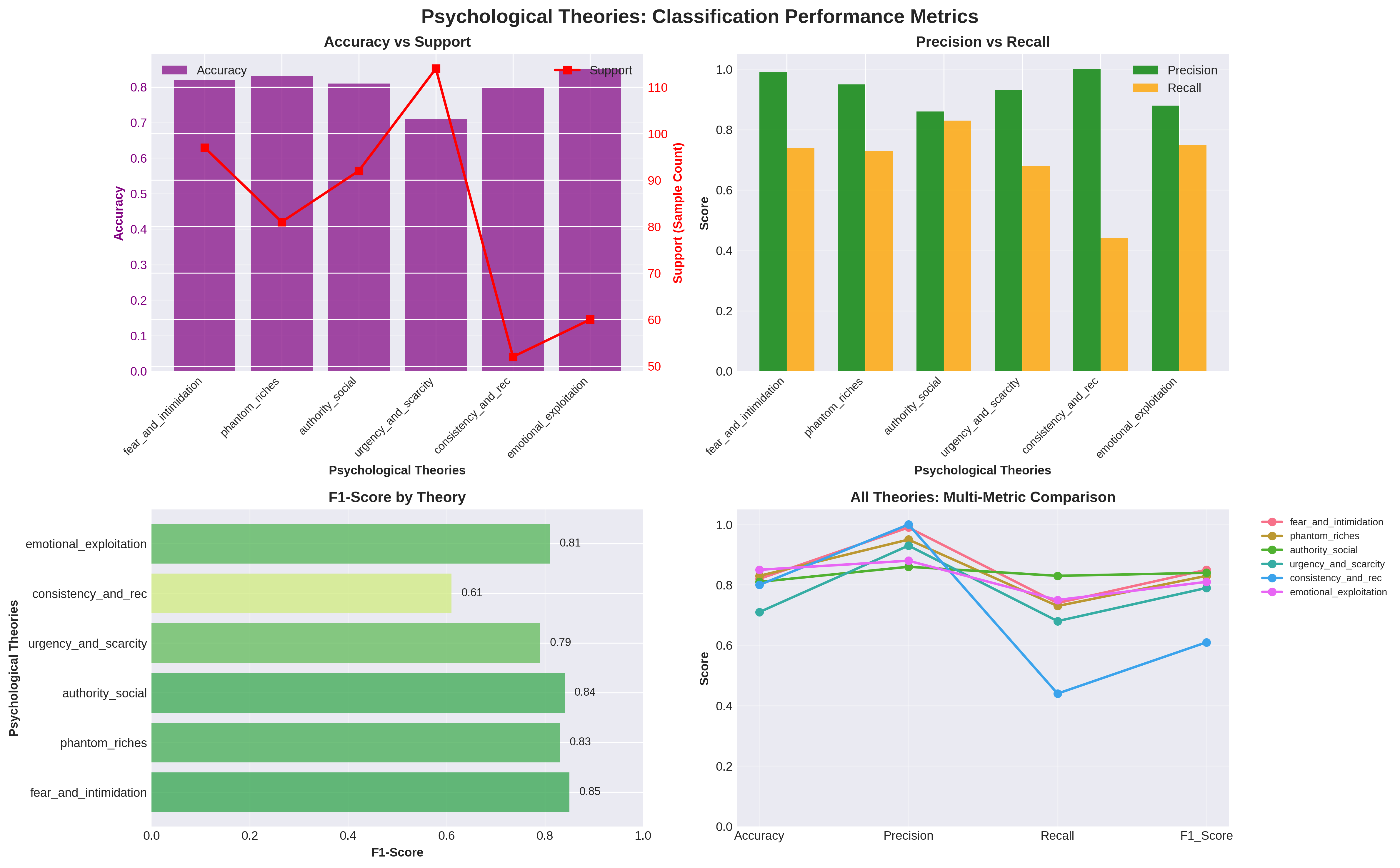
Cybercrime increasingly exploits human cognitive biases in addition to technical vulnerabilities, yet most existing analytical frameworks focus primarily on operational aspects and overlook psychological manipulation. This paper proposes BEACON, a unified dual-dimension framework that integrates behavioral psychology with the tactical lifecycle of cybercrime to enable structured, interpretable, and scalable analysis of cybercrime. We formalize six psychologically grounded manipulation categories derived from Prospect Theory and Cialdini's principles of persuasion, alongside a fourteen-stage cybercrime tactical lifecycle spanning reconnaissance to final impact. A single large language model is fine-tuned using parameter-efficient learning to perform joint multi-label classification across both psychological and tactical dimensions while simultaneously generating human-interpretable explanations. Experiments conducted on a curated dataset of real-world and synthetically augmented cybercrime narratives demonstrate a 20 percent improvement in overall classification accuracy over the base model, along with substantial gains in reasoning quality measured using ROUGE and BERTScore. The proposed system enables automated decomposition of unstructured victim narratives into structured behavioral and operational intelligence, supporting improved cybercrime investigation, case linkage, and proactive scam detection.
Cybercrime has emerged as one of the most pervasive and economically destructive consequences of global digitalization. Contemporary online fraud and deceptionbased crimes now account for unprecedented financial losses worldwide, exceeding trillions of United States dollars (USD) annually (Morgan, 2016), while also inflicting severe psychological, social, and reputational harm on victims. Unlike classical cyberattacks targeting systems and networks, modern cybercrime increasingly exploits human vulnerabilities rather than purely technical weaknesses, relying on deception, persuasion, impersonation, emotional coercion, and trust manipulation as primary attack vectors (Holt, 2019;Yao, Zheng, Wu, Wu, Gao, Wang and Yang, 2025;Sarkar and Shukla, 2023;Sarkar, Singh, Kumar and Shukla, 2023).
Existing cybersecurity frameworks, such as the Cyber Kill Chain and the MITRE ATT&CK framework, provide powerful abstractions for understanding technically sophisticated cyberattacks targeting enterprise systems and critical infrastructure (MITRE Corporation, 2025b,a). However, these models are fundamentally system-centric: they describe how adversaries compromise digital infrastructure, escalate privileges, and exfiltrate data. In contrast, cybercrime, particularly scams, fraud, impersonation, and extortion, primarily targets individual decision-making processes (Louderback and Antonaccio, 2017), often without exploiting any software vulnerability at all. Consequently, the investigative needs of cybercrime differ substantially from those of traditional cyberattacks. Law enforcement agencies must 1 These authors contributed equally to this work. * Corresponding author. Email: gargi.sarkar@research.iiit.ac.in ORCID(s):
understand not only how a crime technically unfolds, but also why victims comply with fraudulent demands at different stages of the offense (Sarkar et al., 2023).
Parallel to these technical models, although not originally formulated for fraud analysis, the theories proposed by Kahneman and Tversky (1979) provide a foundational explanation of economic decision-making under risk and uncertainty, and have since been widely adopted to characterize the cognitive biases exploited in deceptive and fraudulent interactions. Complementing this perspective, Cialdini’s principles of persuasion provide a social-psychological framework for understanding how influence mechanisms, such as authority, scarcity, and social proof, are systematically leveraged in social engineering and cybercrime (Cialdini, 2007). These studies have established that cybercriminals systematically exploit biases such as loss aversion (Ridho, 2024), scarcity (De Bruijn and Antonides, 2022;Chinecherem, 2025), authority (Fehr, Herz and Wilkening, 2013), reciprocity (Falk and Fischbacher, 2006), and emotional dependence (Alshammari, Benson and Batista, 2023).
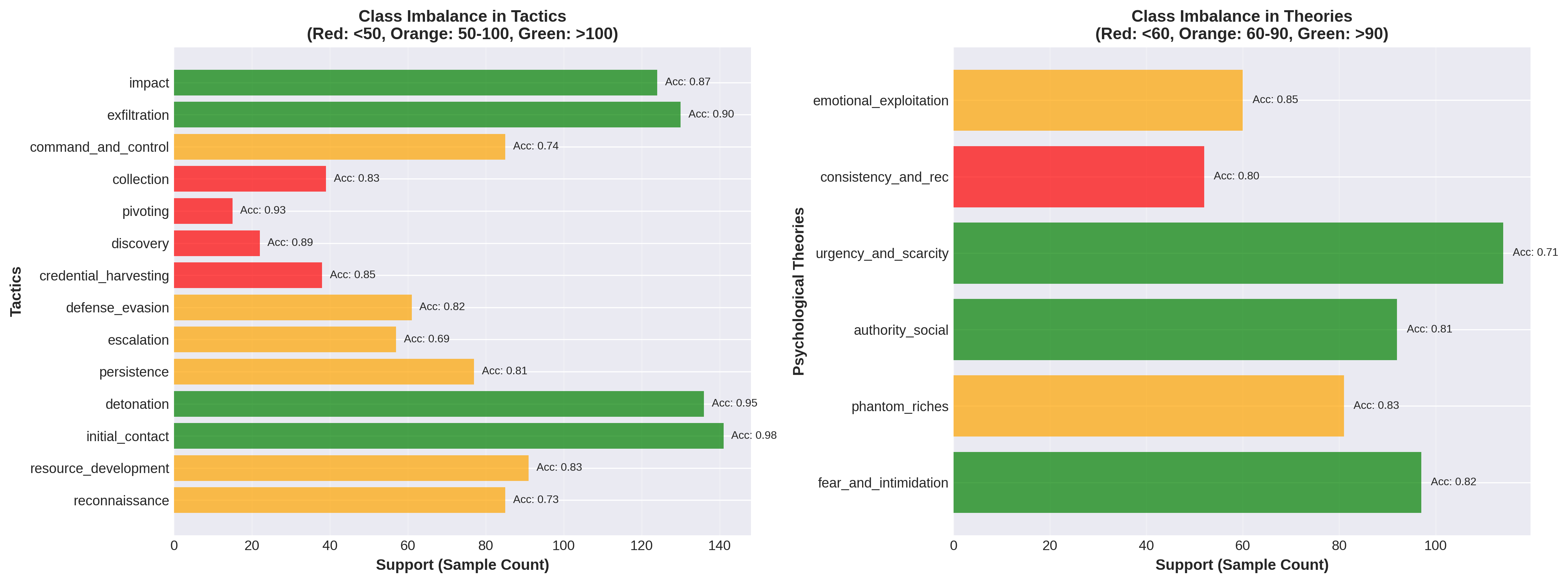
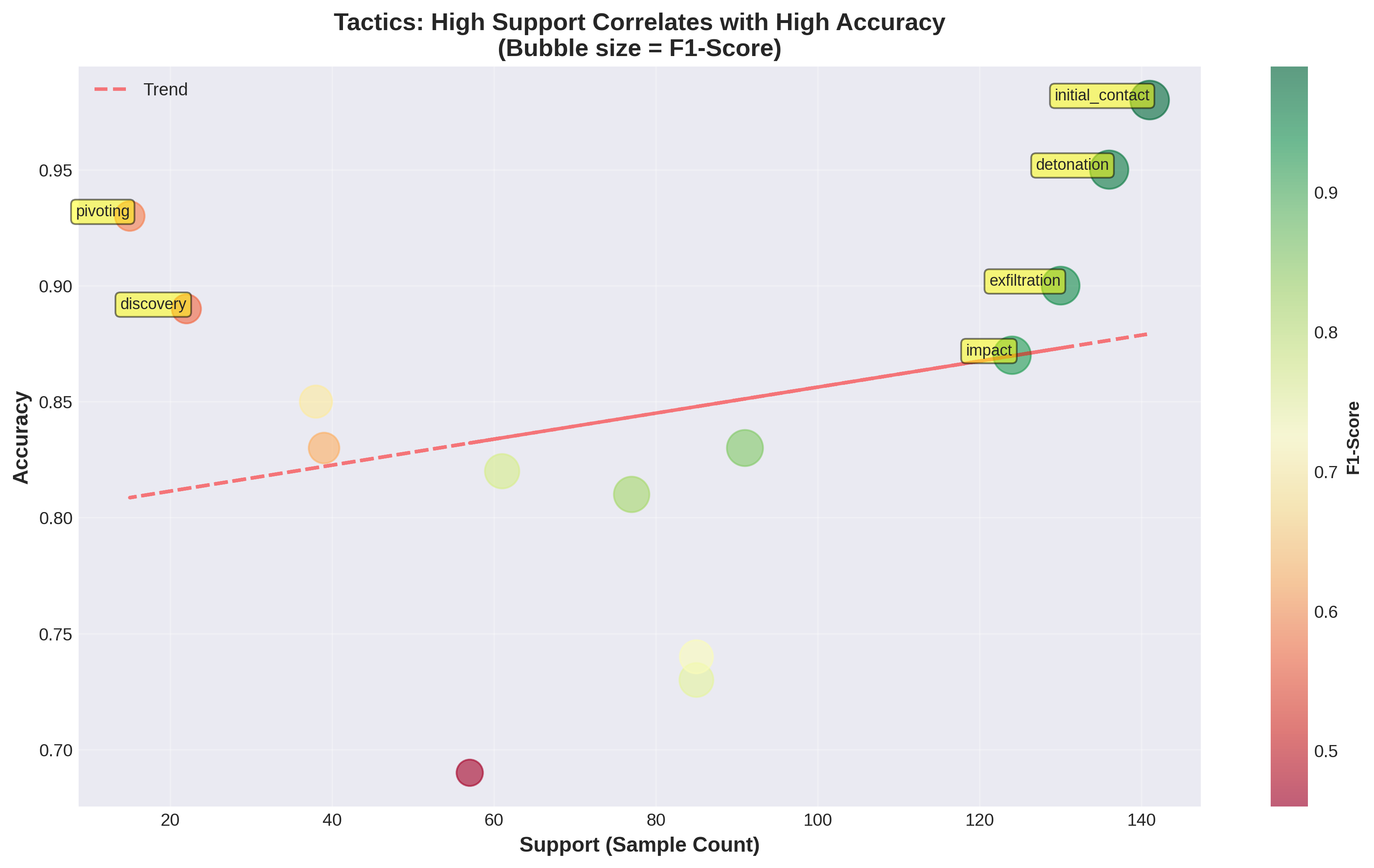
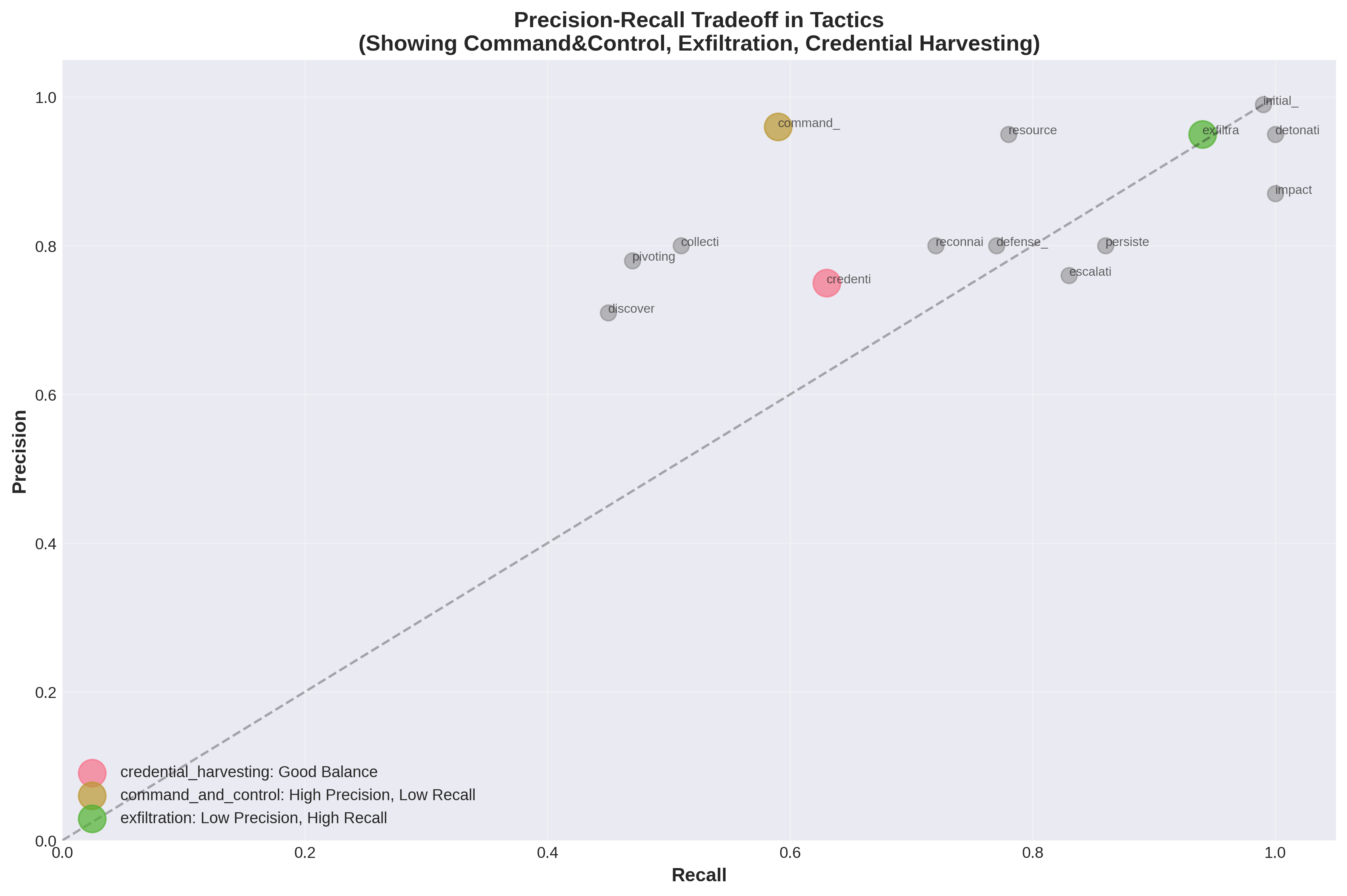
Recent efforts have introduced Tactics, Techniques, and Procedures (TTP)-based lifecycle models tailored specifically for cybercrime investigation, enabling structured representation of 14 operational stages (see Table 1 for a full list of tactics) such as reconnaissance, initial contact, credential harvesting, exfiltration, and impact (Sarkar et al., 2023). Separately, prior studies have examined the role of social influence and cognitive biases in scam victimization (Muscanell, Guadagno and Murphy, 2014;Ma, Ma, Liu, Song, Liang, Xiao and Ye, 2025). However, no existing automated framework jointly models the operational lifecycle of cybercrime and the underlying psychological manipulation This structural disconnect between technical and psychological perspectives represents a critical gap in current cybercrime research and practice. In real-world investigations, cybercrime does not unfold as a purely technical sequence nor as an isolated psychological manipulation; rather, it manifests as a tightly coupled interaction between adversarial operations and human cognition. Yet, existing analytical frameworks lack the ability to jointly model these interacting dimensions in a single, coherent inferential system. As a result, investigators often rely on manual interpretation of unstructured victim narratives, a process that is slow, inconsistent, and difficult to scale.
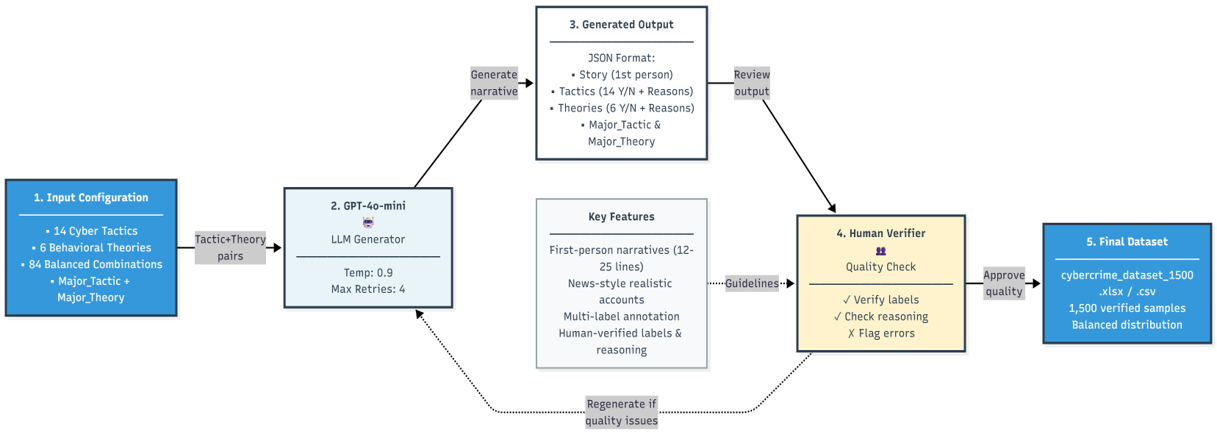
Recent advances in large language models (LLMs) have demonstrated strong capabilities in narrative understanding, reasoning, and structured information extraction from unstructured text. These models offer a promising opportunity to bridge technical and psychological dimensions of cybercrime within a unified analytical framework. However, most existing LLM-based cybercrime studies either focus exclusively on detecting scam content (Jiang, 2024;Roy, Thota, Naragam and Nilizadeh, 2024;Koide, Fukushi, Nakano and Chiba, 2024a;Jamal, Wimmer and Sarker, 2024;Heiding, Schneier, Vishwanath, Bernstein and Park, 2024;Koide, Nakano and Chiba, 2024b;Lau, Liao, Kwok, Xu, Xia and Li, 2012;Bitaab, Karimi, Lyu, Mosallanezhad, Oest, Wang, Bao, Shoshit
This content is AI-processed based on open access ArXiv data.