Cloud-supported Internet of Things (Cloud-IoT) has been broadly deployed in smart grid systems. The IoT front-ends are responsible for data acquisition and status supervision, while the substantial amount of data is stored and managed in the cloud server. Achieving data security and system efficiency in the data acquisition and transmission process are of great significance and challenging, because the power grid-related data is sensitive and in huge amount. In this paper, we present an efficient and secure data acquisition scheme based on CP-ABE (Ciphertext Policy Attribute Based Encryption). Data acquired from the terminals will be partitioned into blocks and encrypted with its corresponding access sub-tree in sequence, thereby the data encryption and data transmission can be processed in parallel. Furthermore, we protect the information about the access tree with threshold secret sharing method, which can preserve the data privacy and integrity from users with the unauthorized sets of attributes. The formal analysis demonstrates that the proposed scheme can fulfill the security requirements of the Cloud-supported IoT in smart grid. The numerical analysis and experimental results indicate that our scheme can effectively reduce the time cost compared with other popular approaches.
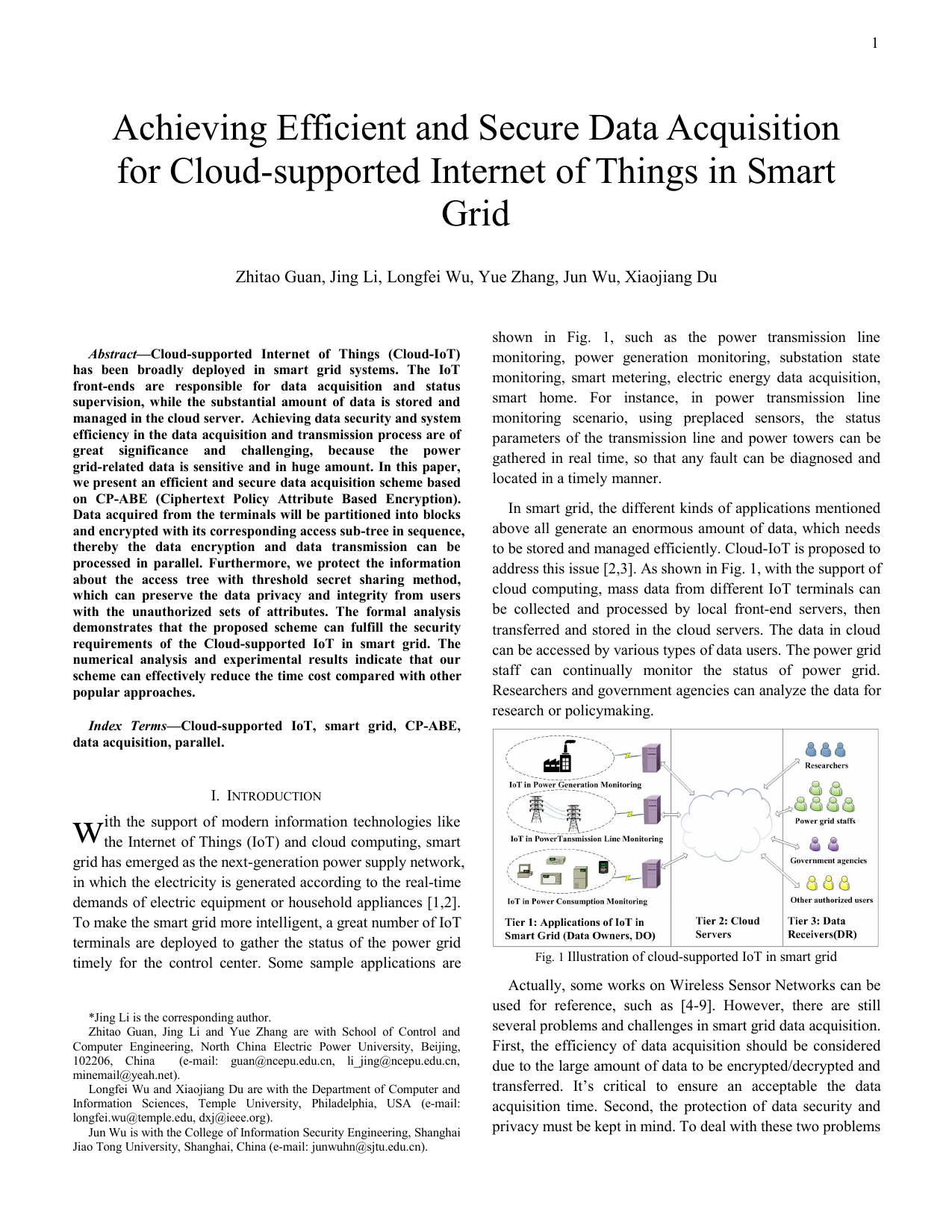
ith the support of modern information technologies like the Internet of Things (IoT) and cloud computing, smart grid has emerged as the next-generation power supply network, in which the electricity is generated according to the real-time demands of electric equipment or household appliances [1,2]. To make the smart grid more intelligent, a great number of IoT terminals are deployed to gather the status of the power grid timely for the control center. Some sample applications are shown in Fig. 1, such as the power transmission line monitoring, power generation monitoring, substation state monitoring, smart metering, electric energy data acquisition, smart home. For instance, in power transmission line monitoring scenario, using preplaced sensors, the status parameters of the transmission line and power towers can be gathered in real time, so that any fault can be diagnosed and located in a timely manner.
In smart grid, the different kinds of applications mentioned above all generate an enormous amount of data, which needs to be stored and managed efficiently. Cloud-IoT is proposed to address this issue [2,3]. As shown in Fig. 1, with the support of cloud computing, mass data from different IoT terminals can be collected and processed by local front-end servers, then transferred and stored in the cloud servers. The data in cloud can be accessed by various types of data users. The power grid staff can continually monitor the status of power grid.
Researchers and government agencies can analyze the data for research or policymaking. Actually, some works on Wireless Sensor Networks can be used for reference, such as [4][5][6][7][8][9]. However, there are still several problems and challenges in smart grid data acquisition. First, the efficiency of data acquisition should be considered due to the large amount of data to be encrypted/decrypted and transferred. It’s critical to ensure an acceptable the data acquisition time. Second, the protection of data security and privacy must be kept in mind. To deal with these two problems Achieving Efficient and Secure Data Acquisition for Cloud-supported Internet of Things in Smart Grid
Zhitao Guan, Jing Li, Longfei Wu, Yue Zhang, Jun Wu, Xiaojiang Du w simultaneously, in this paper, we present an efficient and secure data acquisition scheme based on CP-ABE. The main contributions of our work can be summarized as the following:
We propose a parallel data processing method. Data acquired from the terminals will be partitioned into blocks and encrypted with its corresponding access sub-tree in sequence, thereby the data encryption and data transmission can be processed in parallel. The data decryption process is similar to the process of data encryption.
We introduce the dual secret sharing scheme to protect the access tree information. Only when all of the shares are combined can the secret be recovered. Each of the data blocks holds a share. While the last one share is protected with the other secret sharing scheme.
If the user’s attributes satisfy the threshold function of root node, then the last share will be retrieved. In addition, some users with the unauthorized attributes sets will be filtered out. We realize the privacy-preserving, the data integrity check and the attributes check simultaneously.
We give the security analysis and performance evaluation, which prove that the security of our scheme is no weaker than that of the traditional scheme, and that our scheme can reduce the system response time and users’ waiting time notably.
The rest of this paper is organized as follows. Section 2 introduces the related work. The preliminaries are given in section 3. In section 4, the system model and security model are described. In section 5, we present the details of the proposed scheme. Its security analysis and performance evaluation are conducted in section 6 and section 7, respectively. Section 8 concludes the paper.
Recently, various techniques have been proposed to address the problems of data security and fine-grained access control. In [10], Sahai and Waters proposed the Attribute-Based Encryption (ABE) to realize fine-grained access control on encrypted data. In ABE, the encryption policy is associated with a set of attributes, and the data owner can be offline after data is encrypted. Vipul Goyal et al developed a new cryptosystem for fine-grained sharing of encrypted data in [11] based on Sahai’s work, called Key-Policy Attribute-Based Encryption (KP-ABE). In their scheme, the ciphertext’s encryption policy is associated with a set of attributes, but the attributes that organized into a tree structure (named access tree) are specified by data receivers. In [12], Bethencourt et al proposed the Ciphertext Policy Attribute Based Encryption (CP-ABE). In their work, the data owner constructs the access tree using visitors’ identity information. The user can decrypt the ciphertext only if the attributes in his private key match the access tree.
Owin
This content is AI-processed based on open access ArXiv data.