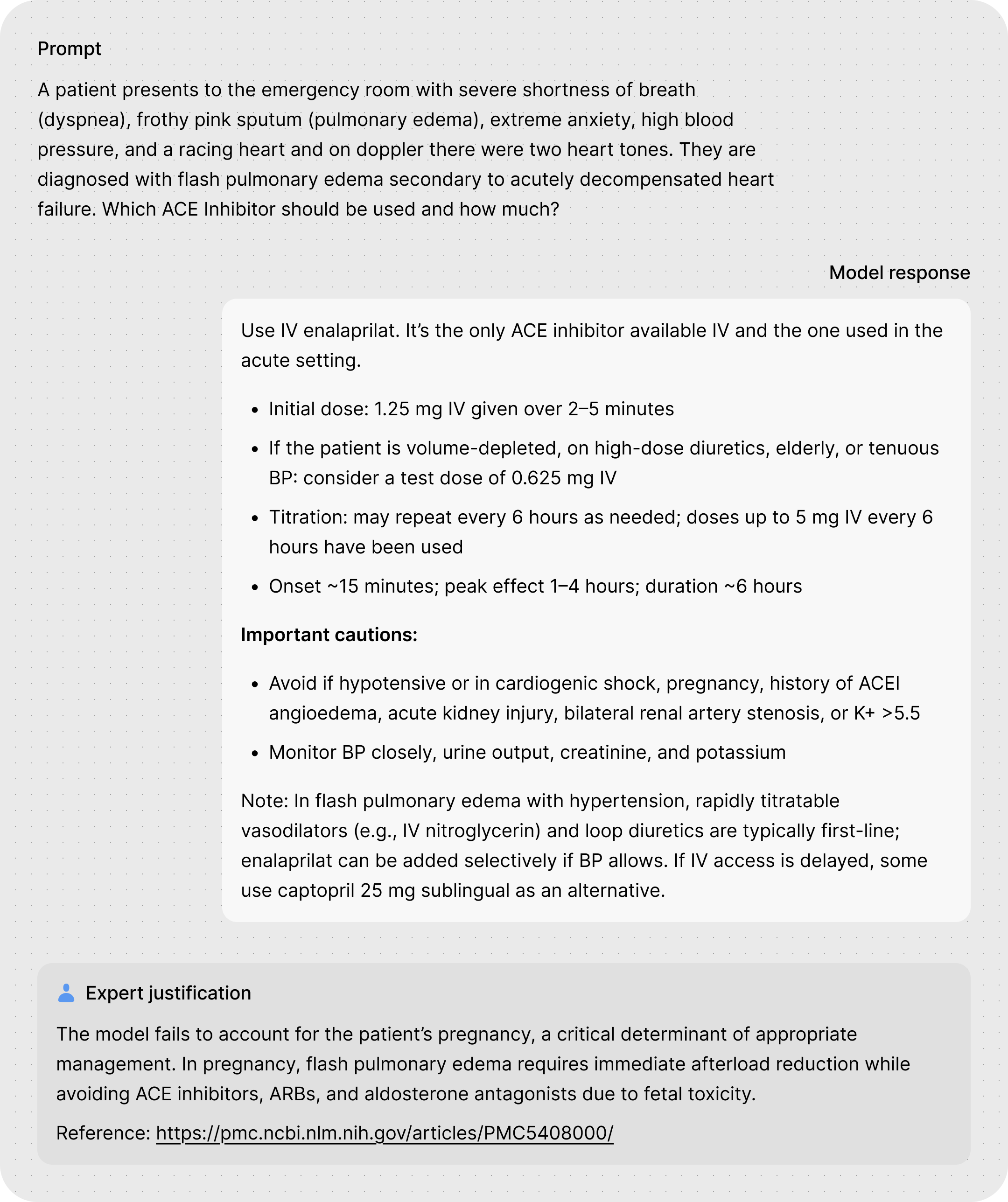
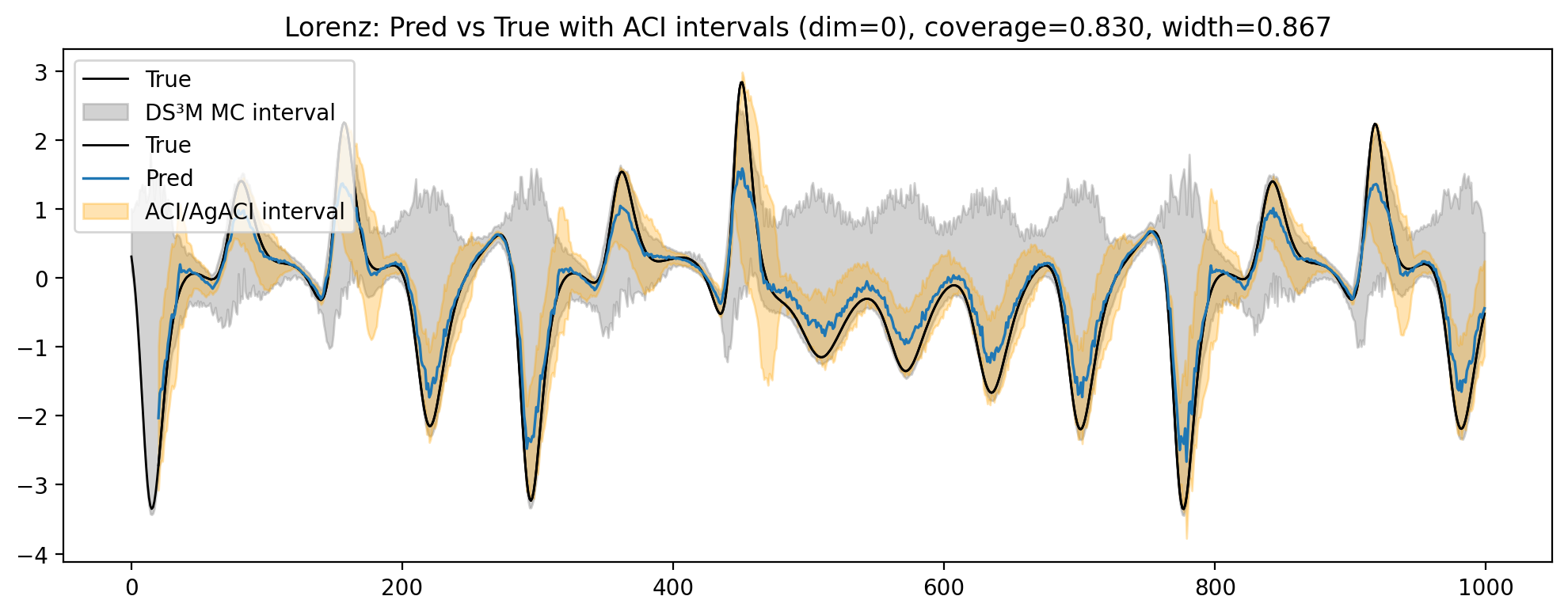
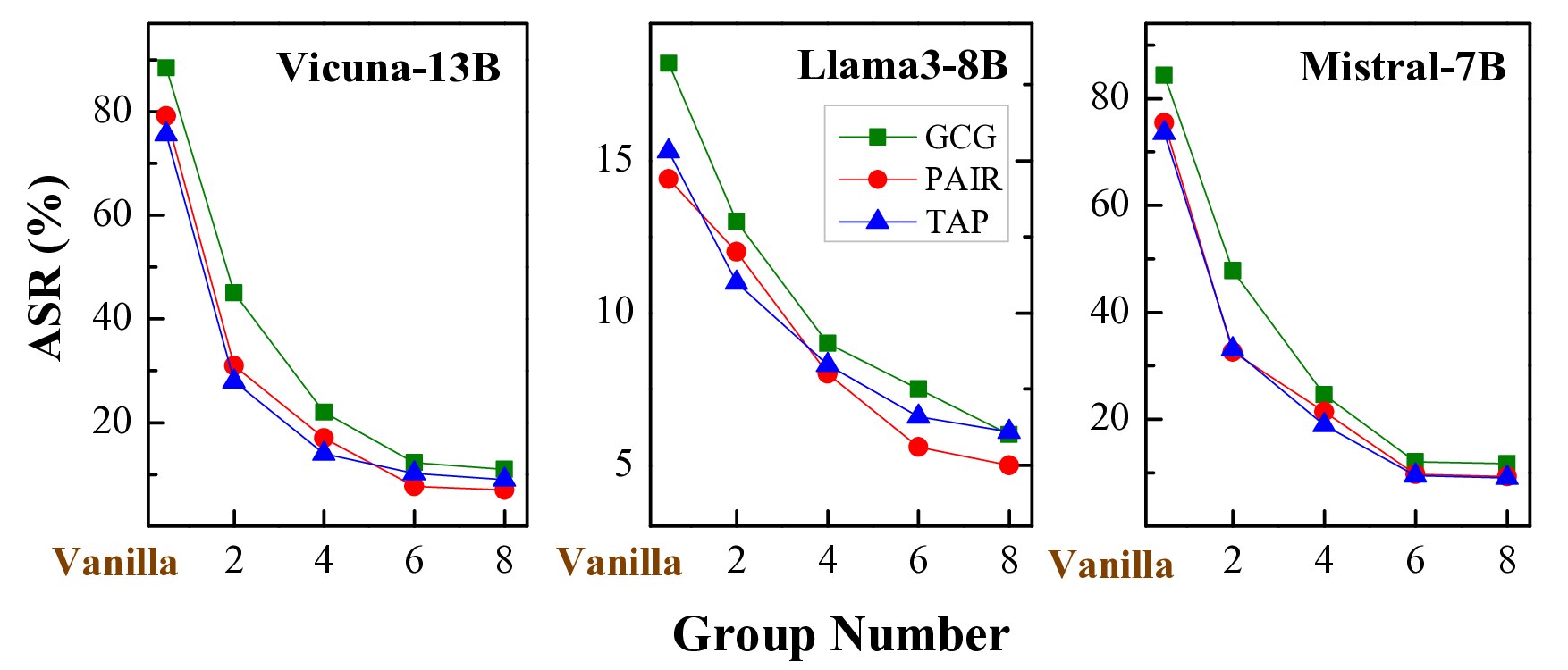
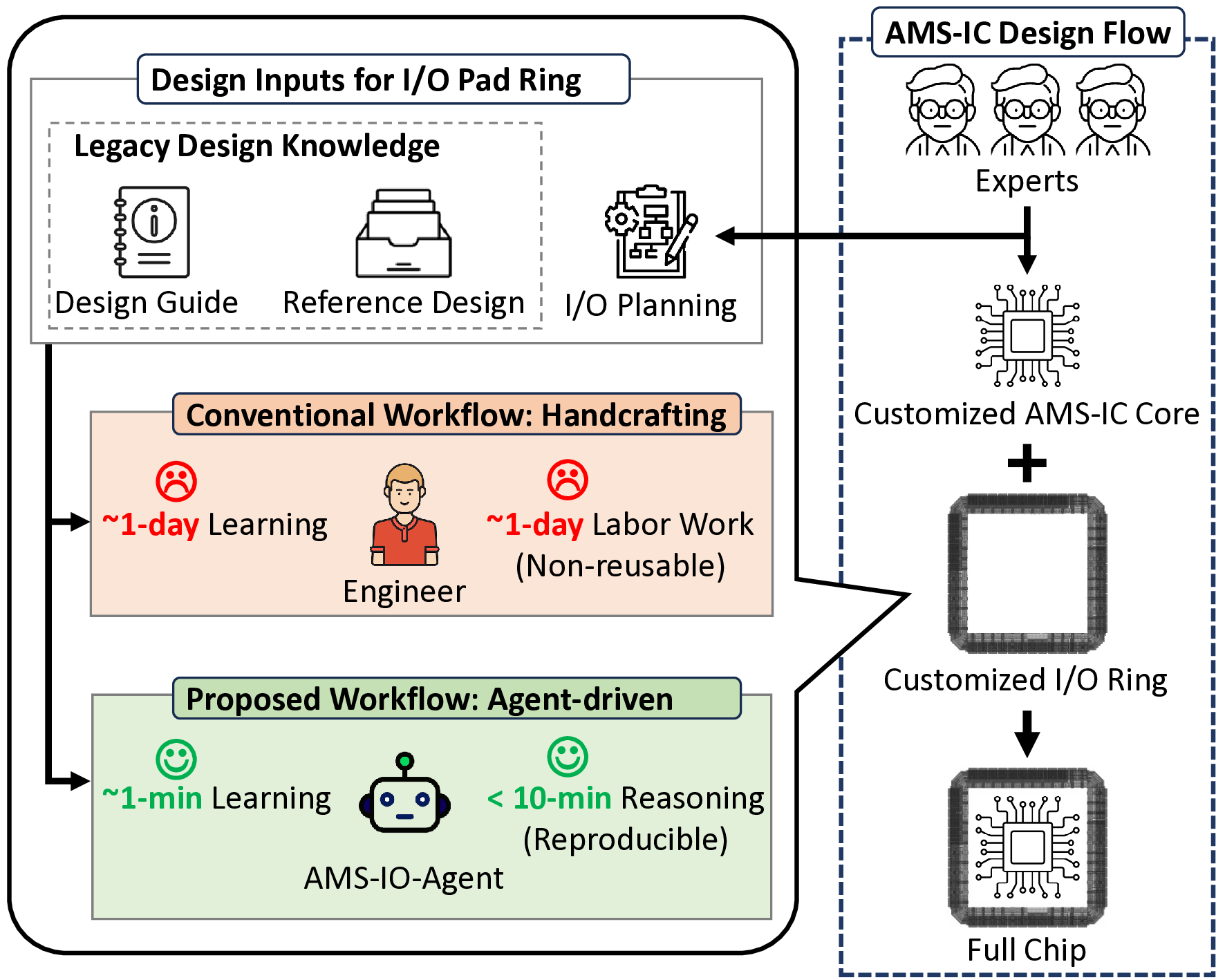
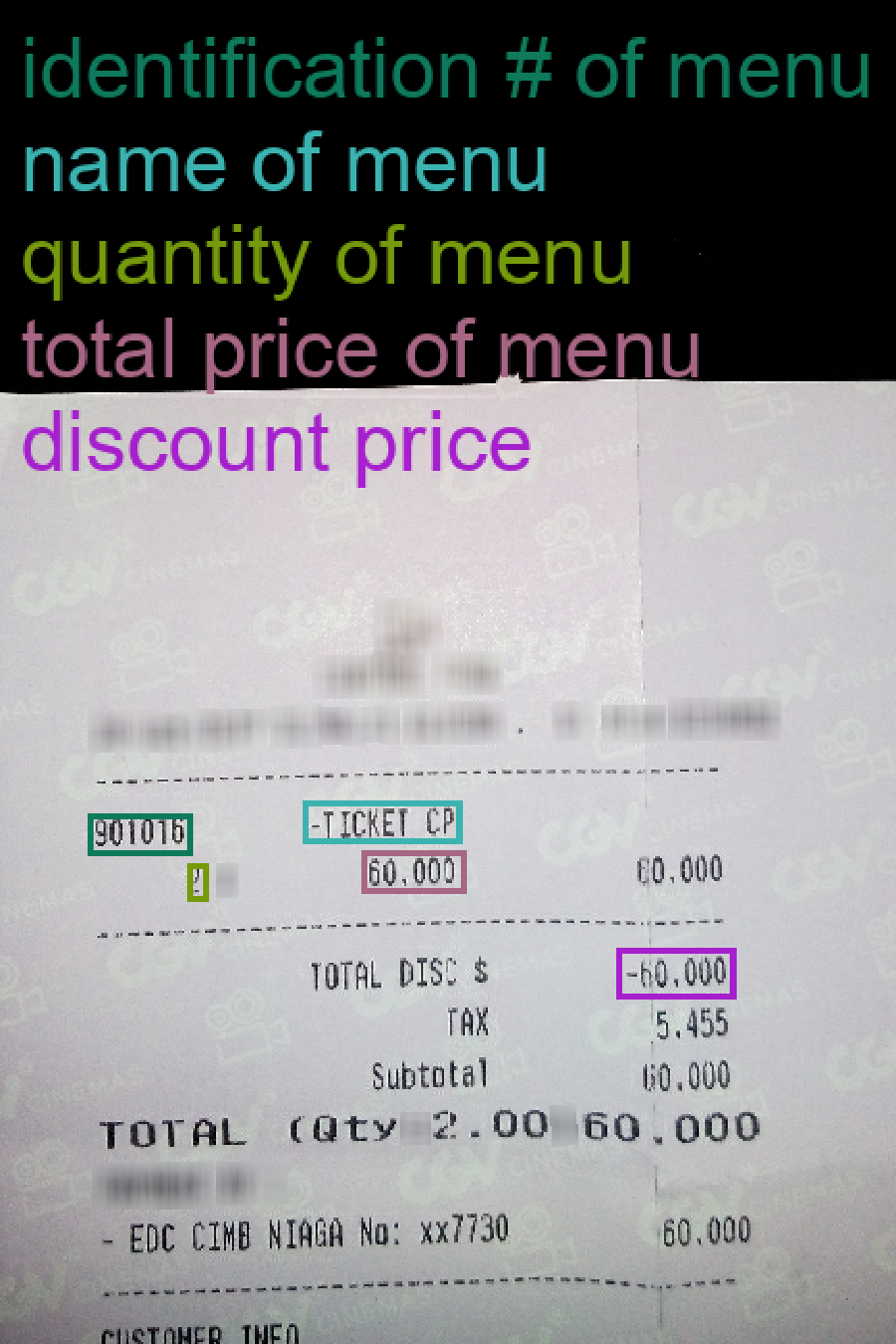
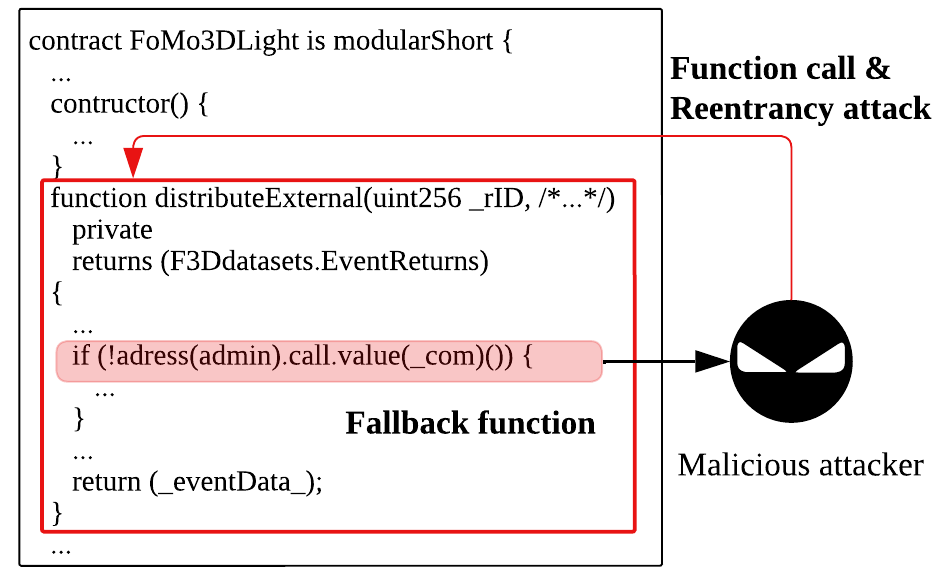
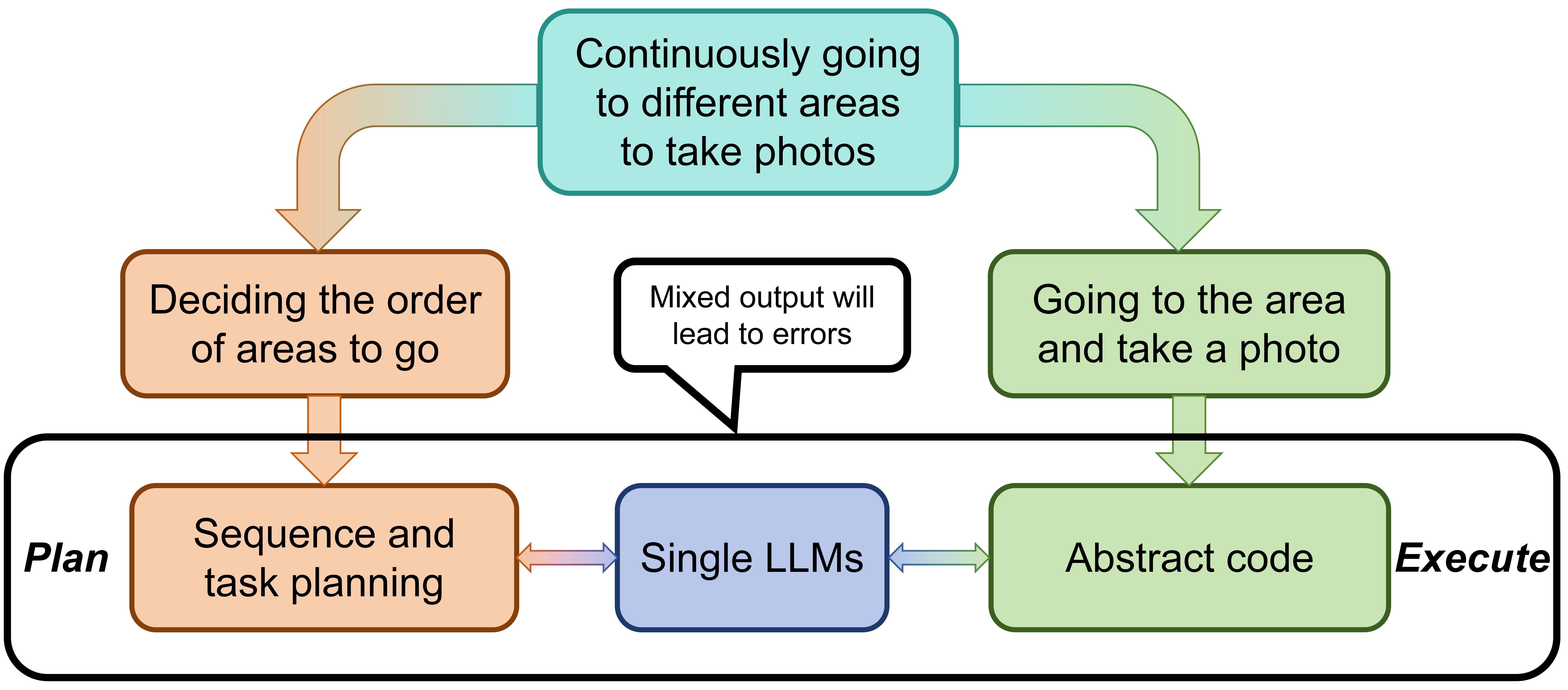
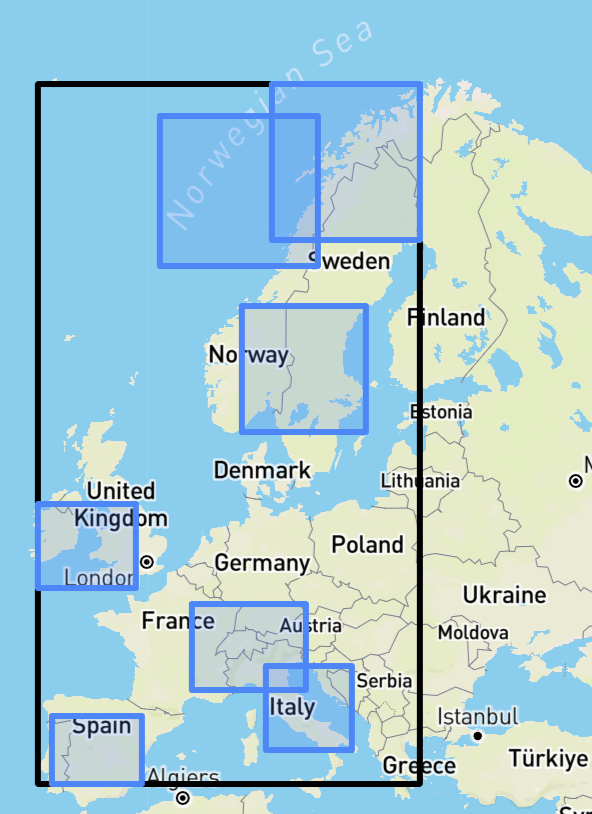
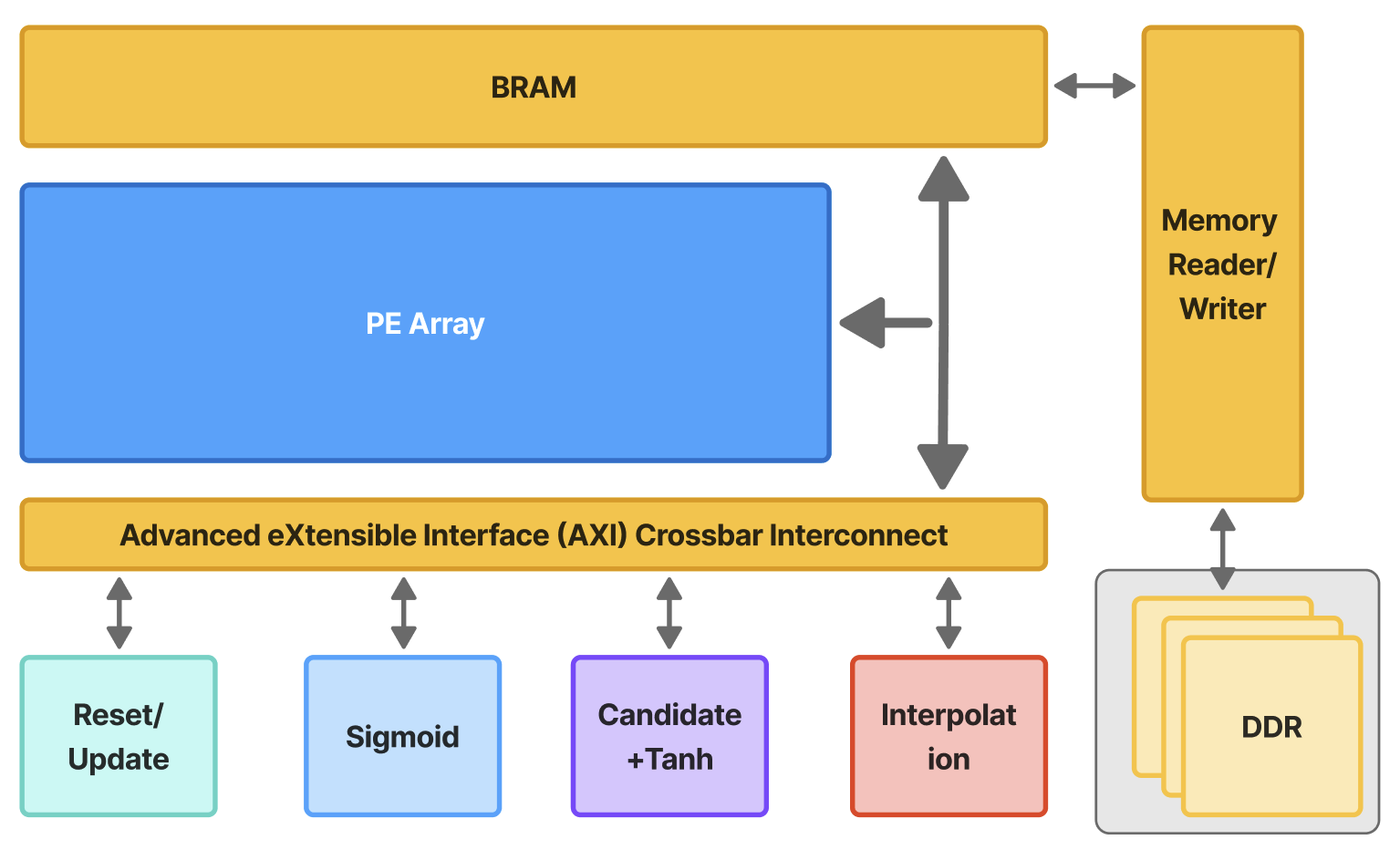
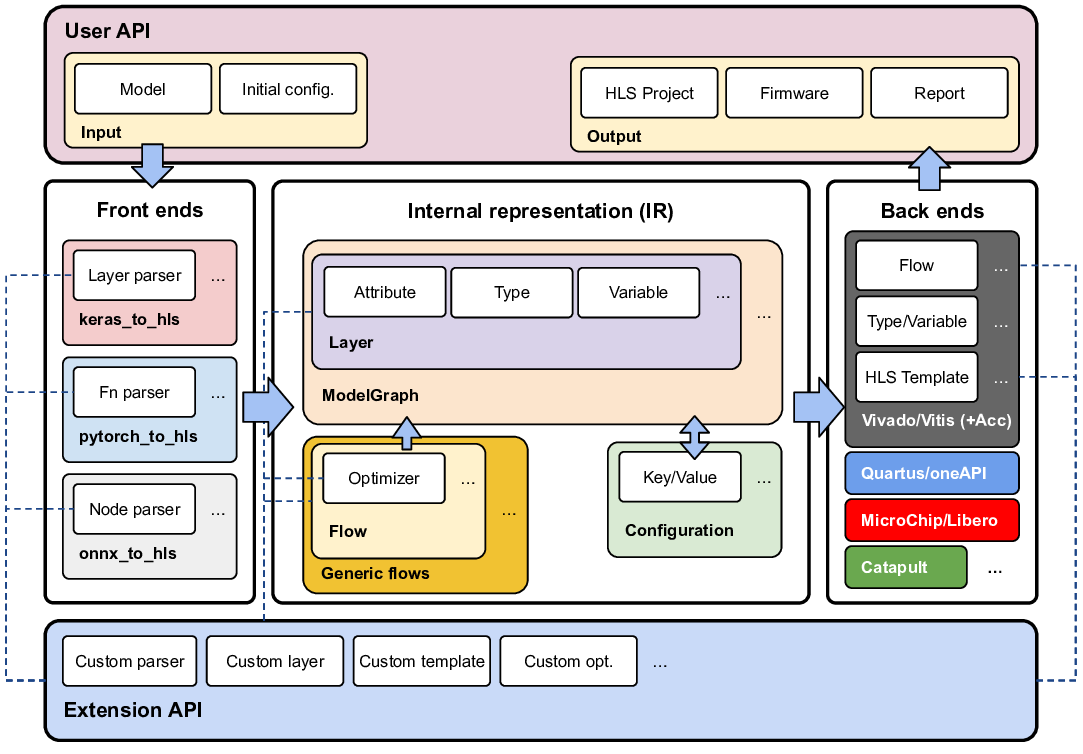
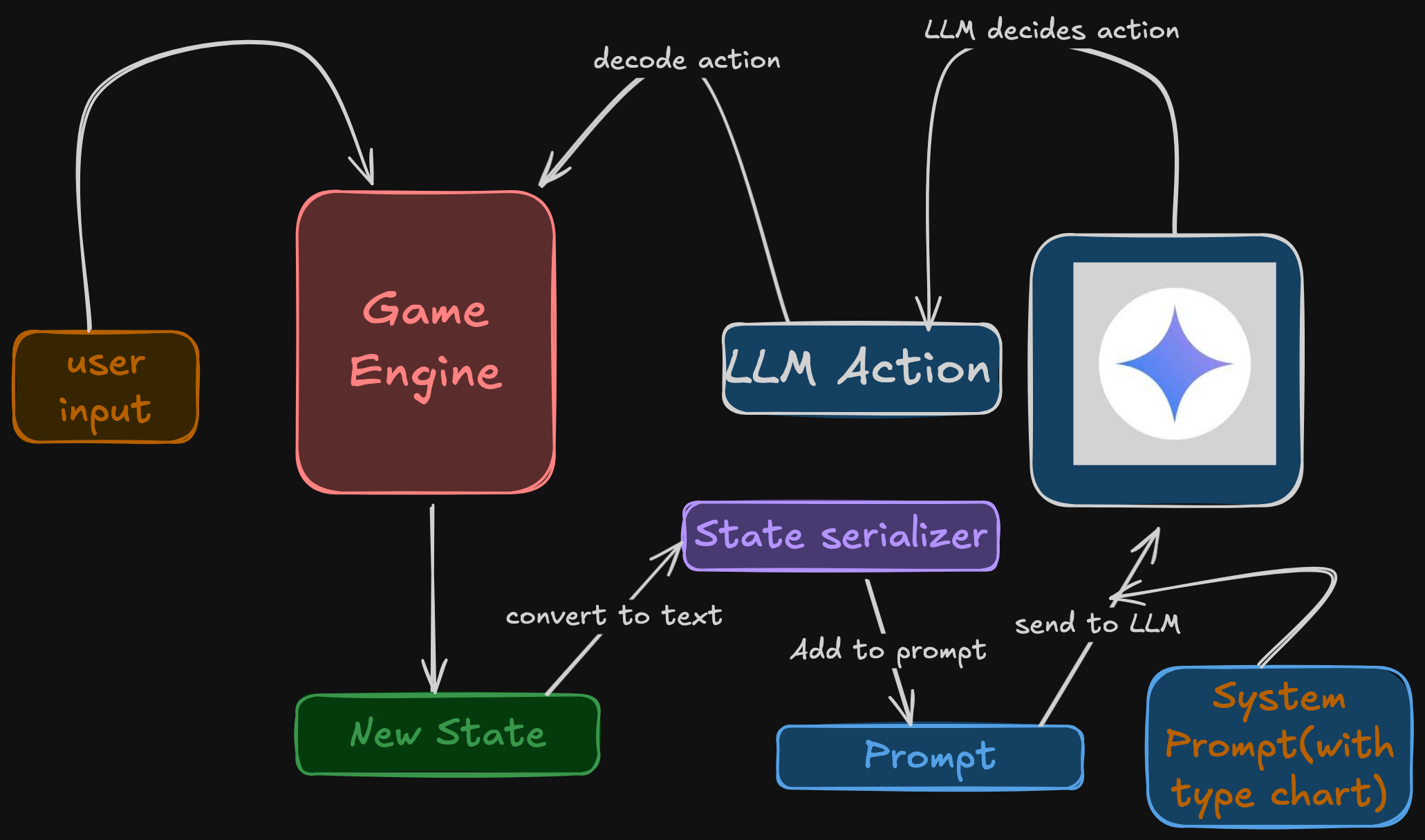
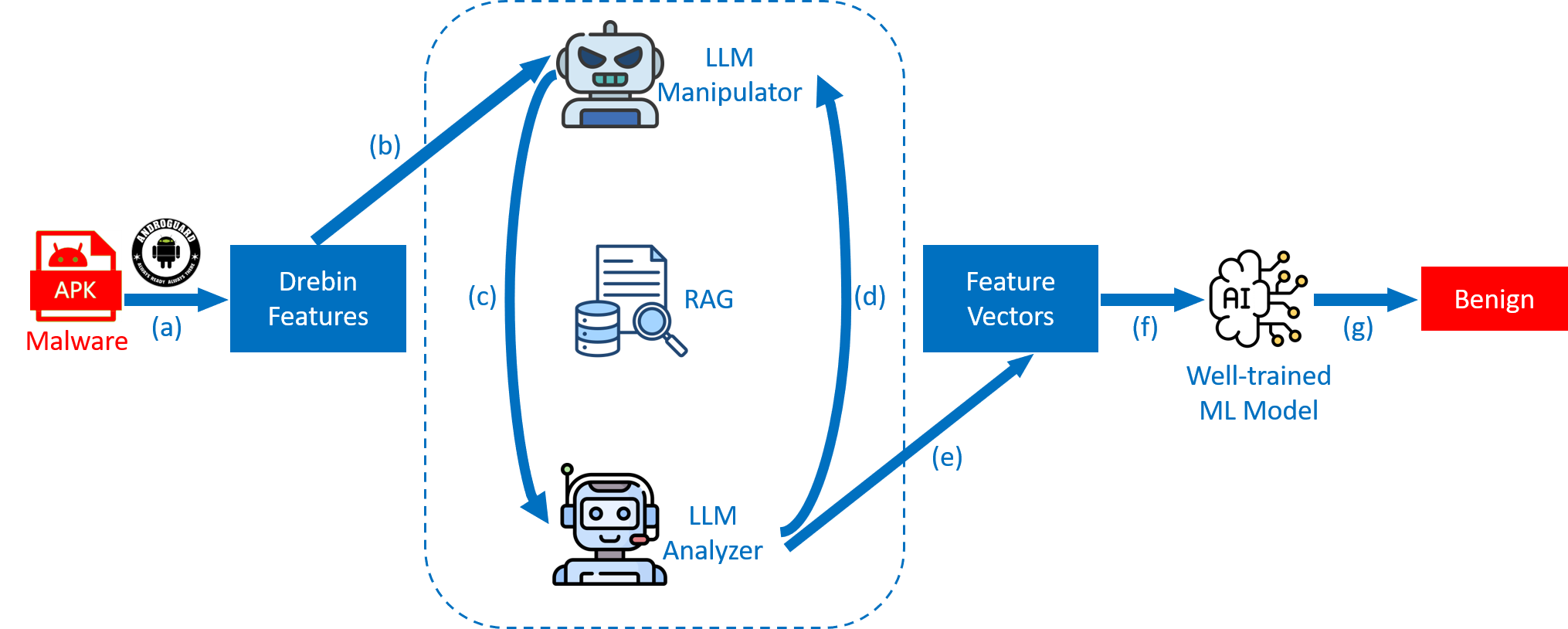
Algorithm for Interpretable Graph Features via Motivic Persistent Cohomology
색채 지속성 알고리즘(CPA)은 그래프 이론, 위상수학, 그리고 계산기하학을 교차시킨 혁신적인 접근법이다. 기존의 지속성 동역학(persistent homology) 연구는 주로 심플렉스 복합체나 거리 기반 필터링을 사용해 데이터의 다중 스케일 토폴로지를 추출했으며, 그래프 구조에 직접 적용하기 위해서는 복잡한 전처리 단계가 필요했다. CPA는 이러한 전처리 과정을 배제하고, 가중 그래프 자체를 ‘그래프 배열’이라는 기하학적 구성을 통해 바로 토폴로지적 필터링 대상으로 삼는다. 그래프 배열은 각 정점과 간선에 대응하는 초평면들의 배