LLM Collusion
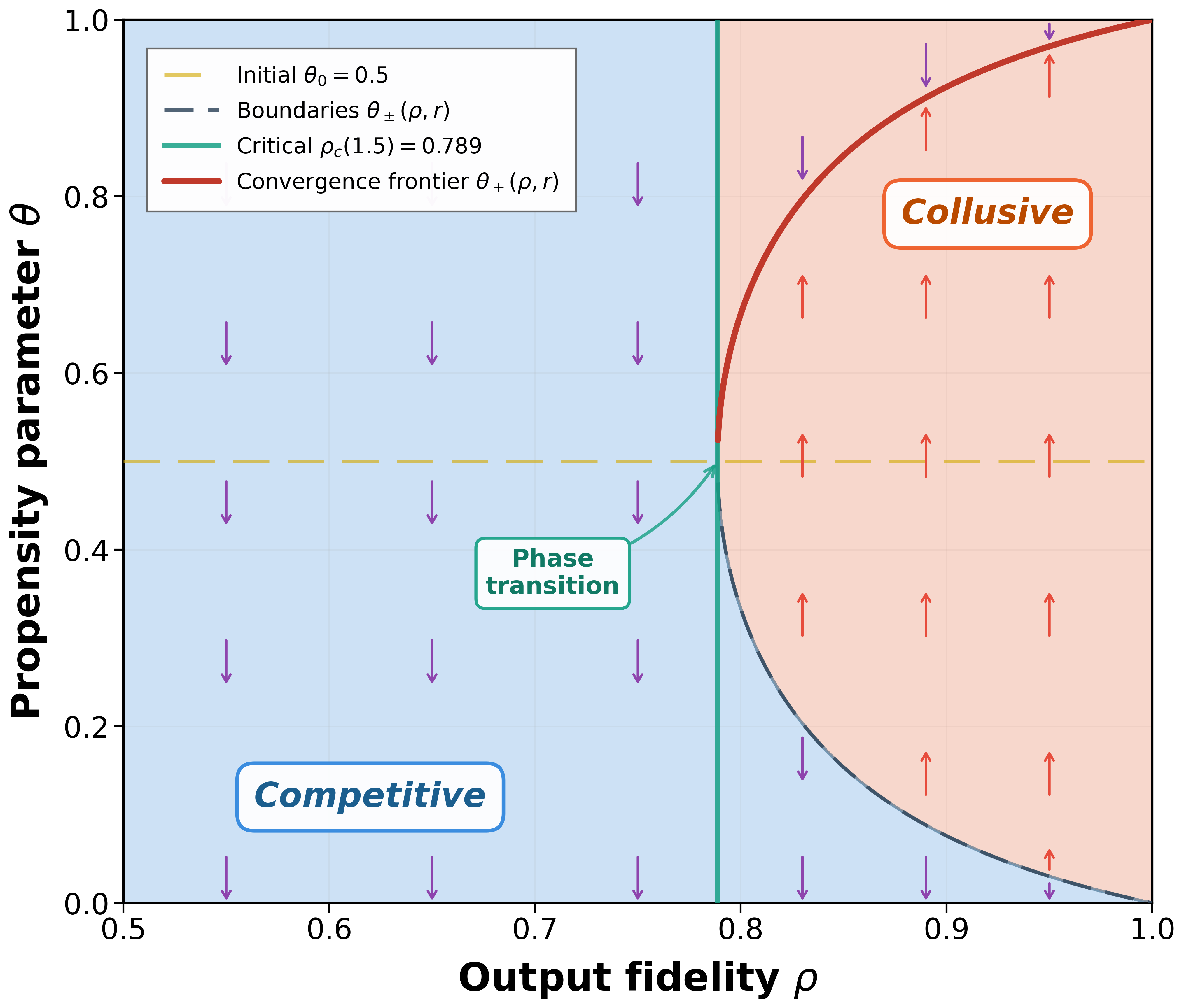
본 논문은 알고리즘 기반 가격 결정 체계에서 대형 언어 모델(LLM)이 불법적인 담합을 유발할 수 있는 잠재적 위험에 대해 깊이 있게 분석하고 있습니다. 이 연구는 LLM의 공유된 지식 인프라와 데이터 집적 정책이 어떻게 시장 수준에서 조율되지 않은 협력을 가능하게 하는지, 그리고 이러한 메커니즘은 어떻게 실제 비즈니스 환경에서 위험성을 높이는지를 설명하고 있습니다. 기술적 혁신성 본 논문의 주요 기술적 혁신성은 LLM이 가격 책정에 활용될 때 발생할 수 있는 콜루션 위험을 이론적으로 분석하는 것입니다. 특히, 본 연구는 LLM이